One Piece
In this post, we will look into the room “One Piece” from TryHackMe, which can be found on https://tryhackme.com
Scan
As always, the first thing to do is to scan the target. After a quick scan, you get:
catsec@kali:~$ sudo nmap -A 10.10.81.215
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-02 21:53 CET
Nmap scan report for localhost (10.10.81.215)
Host is up (0.042s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 187 Jul 26 06:27 welcome.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.8.101.184
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 01:18:18:f9:b7:8a:c3:6c:7f:92:2d:93:90:55:a1:29 (RSA)
| 256 cc:02:18:a9:b5:2b:49:e4:5b:77:f9:6e:c2:db:c9:0d (ECDSA)
|_ 256 b8:52:72:e6:2a:d5:7e:56:3d:16:7b:bc:51:8c:7b:2a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: New World
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=11/2%OT=21%CT=1%CU=40088%PV=Y%DS=2%DC=T%G=Y%TM=5FA071C
OS:6%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=103%TI=Z%CI=I%II=I%TS=A)OPS
OS:(O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST1
OS:1NW7%O6=M505ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN
OS:(R=Y%DF=Y%T=40%W=6903%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 42.75 ms localhost (10.8.0.1)
2 42.76 ms localhost (10.10.81.215)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .We can see 3 different open ports:
- 21 FTP
- 22 SSH
- 80 HTTP
We can also notice that the FTP port allows you to log anonymously so this should be the go to.
Port 21: FTP
By logging to the FTP server, you can enumerate what it contains, you get:
catsec@kali~$ ftp 10.10.81.215
Connected to 10.10.81.215.
220 (vsFTPd 3.0.3)
Name (10.10.81.215:catsec): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 187 Jul 26 06:27 welcome.txt
226 Directory send OK.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Jul 26 06:41 .
drwxr-xr-x 3 0 0 4096 Jul 26 06:41 ..
drwxr-xr-x 2 0 0 4096 Jul 26 06:42 .the_whale_tree
-rw-r--r-- 1 0 0 187 Jul 26 06:27 welcome.txt
226 Directory send OK.You can see 2 interesting information:
- A file named “welcome.txt”
- A hidden directory named “.the_whale_tree”
You then can extract the file:
get <FILE_NAME>
And go to the hidden directory.
By enumerating the hidden directory, you get:
ftp> get welcome.txt
local: welcome.txt remote: welcome.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for welcome.txt (187 bytes).
226 Transfer complete.
187 bytes received in 0.01 secs (16.0022 kB/s)
ftp> cd the_whale_tree
550 Failed to change directory.
ftp> cd .the_whale_tree
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jul 26 06:42 .
drwxr-xr-x 3 0 0 4096 Jul 26 06:41 ..
-rw-r--r-- 1 0 0 8652 Jul 26 06:42 .road_poneglyph.jpeg
-rw-r--r-- 1 0 0 1147 Jul 26 06:42 .secret_room.txt
226 Directory send OK.
ftp> get .secret_room.txt
local: .secret_room.txt remote: .secret_room.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for .secret_room.txt (1147 bytes).
226 Transfer complete.
1147 bytes received in 0.00 secs (15.6266 MB/s)
You can see 2 other interesting files, note that both are hidden:
- “.road_poneglyph.jpeg”
- “.secret_room.txt”
You can then extract these 2 files.
Now that you got 3 different files from the FTP server, you need to check each of them:
File: welcome.txt
The file “welcome.txt” contains:
catsec@kali~$ cat welcome.txt
Welcome to Zou. It is an island located on the back of a massive, millennium-old elephant named Zunesha that roams the New World.
Except this, there is not much to say about this island.
catsec@kali~$To be honest, this is just a reference to One Piece Zou “island”. It just serves as an introduction as this island has an important role in the One Piece history.
File: .sercret_room.txt
The file “.secret_room.txt” has a promising name and contains:
catsec@kali~$ cat .secret_room.txt
Inuarashi: You reached the center of the Whale, the majestic tree of Zou.
Nekomamushi: We have hidden this place for centuries.
Inuarashi: Indeed, it holds a secret.
Nekomamushi: Do you see this red stele ? This is a Road Poneglyph.
Luffy: A Road Poneglyph ??
Inuarashi: There are four Road Poneglyphs around the world. Each of them gives one of the key to reach Laugh Tale and to find the One Piece.
Luffy: The One Piece ?? That's my dream ! I will find it and I will become the Pirate King !!!
Nekomamushi: A lot have tried but only one succeeded over the centuries, Gol D Roger, the former Pirate King.
Inuarashi: It is commonly known that both Emperors, Big Mom and Kaido, own a Road Poneglyph but no one knows where is the last one.
Nekomamushi: The other issue is the power of Big Mom and Kaido, they are Emperor due to their strength, you won't be able to take them down easily.
Luffy: I will show them, there can be only one Pirate King and it will be me !!
Inuarashi: There is another issue regarding the Road Poneglyph.
Nekomamushi: They are written in an ancient language and a very few people around the world can actually read them. This file appears to be a dialog between 3 people:
- Luffy
- Inuarashi
- Nekomamushi
Let’s remind 2 things:
As described in Task 1 description, the purpose of this room is to find the One Piece and hence to become the Pirate King.
As described in Task 2 description, in order to reach Laugh Tale, the island where the One Piece is located, you must collect the 4 Road Poneglyphs.
So this file gives valuable information:
- There is 1 Road Poneglyph there (other file is named “.road_poneglyph.jpeg”).
- Big Mom owns a Road Poneglyph.
- Kaido owns a Road Poneglyph.
- No one knows where is the last Road Poneglyph.
- Each Road Poneglyph gives one of the keys to reach Laugh Tale (target).
- Road Poneglyphs are written in an ancient language (meaning encoded and/or encrypted)
- This file gives the answer to Task 2 Question 1.
Info: In the Manga, there is also a Road Poneglyph on Zou. Both Big Mom and Kaido owns a Road Poneglyph. And the location of the last Road Poneglyph has not been revealed yet.
File: .road_poneglyph.jpeg
By looking at the picture this is what you will see:

Info: This is the first Road Poneglyph we get to see in the Manga (Zou island).
At this point, steganography must seem obvious, as you know there are various ways and places where you can hide data within an image.
For this case, you need to use steghide with no password to reveal its hidden message:
steghide extract -sf <FILE_NAME>
You get a file named “road_poneglyph1.txt” which, as promised, is encoded or encrypted or both.
catsec@kali~$ steghide extract -sf .road_poneglyph.jpeg
Enter passphrase:
wrote extracted data to "road_poneglyphe1.txt".
catsec@kali~$ cat road_poneglyphe1.txt
FUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKInfo: In the manga, the Poneglyphs are written in an ancient language. Only one person is known to be able to read them.
You can try to decode it as it seems to be base32 encoded, followed by morse code encoded, followed by etc.
But I need to be honest, this is a rabbit hole.
As in the One Piece world, 1 Road Poneglyph alone is pointless. You need to get the 4 of them to be able to decode them all.
This is hinted by the sentence “Each of them gives one of the keys to reach Laugh Tale” of the “.secret_room.txt” file.
Conclusion — Port 21: FTP
We got 2 valuable information from this FTP server:
- 1 Road Poneglyph
- The location of 2 other Road Poneglyphs
Now it is time to look at the web server as we don’t know yet the ssh username and we don’t know the password either so brute forcing it is definitely a bad idea.
Port 80: HTTP
Page: /index.html
By going to the webpage, you arrive on this page:
By reading the text, you can know what you need to do next:
- “You need to find the Log Pose to be able to reach the next island.”
You probably got tempted to enumerate with gobuster or another similar tool to find other webpages. But if you do enumerate like this, you will only find 2 directories, “/images” and “/css” and you may be stuck there.
You could decide to dig deeper and to look for a domain name or subdomains but you wouldn’t find anything.
If you give a look at the source code, you will find an interesting comment:
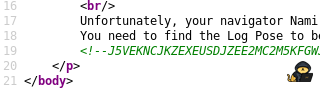
The comment seems to be base32 encoded. If you decode it you get:
catsec@kali~$ echo 'J5VEKNCJKZEXEUSDJZEE2MC2M5KFGWJTJMYFMV2PNE2UMWLJGFBEUVKWNFGFKRJQKJLUS5SZJBBEOS2FON3U4U3TFNLVO2ZRJVJXARCUGFHEOS2YKVWUWVKON5HEOQLVKEZGI3S2GJFEOSKTPBRFAMCGKVJEIODQKJUWQ3KMIMYUCY3LNBGUWMCFO5IGYQTWKJ4VMRK2KRJEKWTMGRUVCMCKONQTGTJ5' | base32 -d
OjE4IVIrRCNHM0ZgTSY3K0VWOi5FYi1BJUViLUE0RWIvYHBGKEswNSs+WWk1MSpDT1NGKXUmKUNoNGAuQ2dnZ2JGISxbP0FURD8pRihmLC1AckhMK0EwPlBvRyVEZTREZl4iQ0Jsa3M=The result string seems to be base64 encoded this time. If you decode it you get:
catsec@kali~$ echo 'OjE4IVIrRCNHM0ZgTSY3K0VWOi5FYi1BJUViLUE0RWIvYHBGKEswNSs+WWk1MSpDT1NGKXUmKUNoNGAuQ2dnZ2JGISxbP0FURD8pRihmLC1AckhMK0EwPlBvRyVEZTREZl4iQ0Jsa3M=' | base64 -d
:18!R+D#G3F`M&7+EV:.Eb-A%Eb-A4Eb/`pF(K05+>Yi51*COSF)u&)Ch4`.CgggbF!,[?ATD?)F(f,-@rHL+A0>PoG%De4Df^"CBlksFinally, it looks like base85 encoded and if you decode it you get:
Nami ensures there are precisely 3472 possible places where she could have lost it.Alright, you get a sentence which is definitely a hint.
You also have a hint in the question itself:
- “Only Sea, It’s Not Terrible”
For this last one, most of you noticed the capital letters and notice that this hint was suggesting OSINT.
So let’s remind what we know:
- Webpage text: “You need to find the Log Pose”.
- There are precisely 3472 possible places where it could be.
- Question hint: “OSINT”.
- Enumeration seems pointless.
Open-Source Intelligence
Alright, so now that we know we need to do a bit of OSINT. The first thing to figure out is: “What are we looking for ?”
Actually I realised, I created an unwanted rabbit hole right here that a lot followed. They found some of the room answers online.
Indeed it’s possible to find/deduce almost all of the answers with OSINT.
Only 2 answers cannot be found without properly hacking the machine.
And as the word “Apache” appears in the following questions, people guessed there was something to do with the website.
Indeed, there is a way to sail to another island and to explore the Apache Sea, actually there are even 2 ways.
So what is the first way ?
First, we know we need to do some OSINT to find something. According to the webpage text, we need to find something called a “Log Pose”. And there is this weird number “3472”.
And now, if you think about what you have done so far:
For most it could be summed up as:
- Check the webpage
- Check the source code
- Enumeration (pages/subdomains/domains)
- Give a look at the files in /images and /css
We will deal with the files from /images and /css a bit later as it is the second way to proceed so let’s exclude them for now.
There is only one of the above options that could give a different output:
- “Enumeration”
To get a different result, there are not so many possiblities, you would need one of the following:
- Different extensions
- Different wordlist
Now let’s keep those 2 possiblities in mind and think about this mysterious number “3472” associated with the word “places”. What could it represent ?
- 3472 extensions ? Highly unlikely.
- 3472 ? Wordlist ? Here there may be something. Could that be the number of entries ?
So what about trying to find a list online with 3472 entries that somehow is a “Log Pose” (remember, this is the name used in the webpage text).
You could google something like “Log Pose list 3472” or similar looking stuff but it won’t give you anything interesting as the google indexing for the webpage containing it is not so great.
Maybe one day it will show up as the first result but let me doubt it, our keywords are “list”, “3472”, “One Piece” and “Log Pose” after all.
Hopefully, there is a famous website that can help you whenever you are looking for computer related stuff such as codes or lists.
I’m sure you already know it: GitHub
Let’s go to GitHub and limit our research to this website, let’s search for “Log Pose” as it is supposed to be the name itself:
https://github.com/search?o=desc&q=Log+Pose&s=&type=RepositoriesWe get 31 results (the number of results may change depending on when you are reading this), not so bad.
You can look at them individually or sort them by “Release Date” to check the latest ones.
Both case scenario, you should find one that catches you eye:
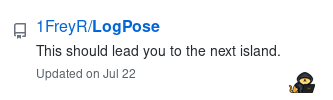
The description is “This should lead you to the next island.”. Perfect ! This is what we want to do.
Info: You also could have noticed the almost similar usernames between GitHub and TryHackMe.
If you open this repository, you will see this:
https://github.com/1FreyR/LogPose
It contains a txt file so let’s give it a look:
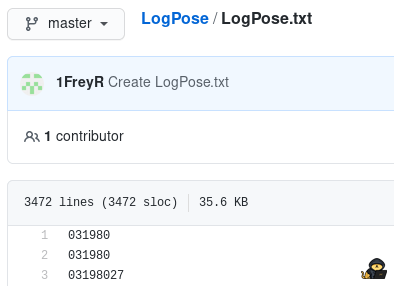
https://github.com/1FreyR/LogPose/blob/master/LogPose.txt
At this point, you know that you found what you were looking for, a list with 3472 entries that is somehow a “Log Pose”.
Get this list and save it into a file.
Now it is time to use it !
Enumeration
In this situation, with a list like this, you should be tempted to use it for enumeration, so let’s do that.
You will get this result:
catsec@kali~$ gobuster dir -u 10.10.81.215 -w LogPose.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.81.215
[+] Threads: 10
[+] Wordlist: LogPose.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/02 22:11:46 Starting gobuster
===============================================================
===============================================================
2020/11/02 22:12:03 Finished
===============================================================Nothing has been found. There are 2 possibilities, this is a domain list (either subdomain or domain names) or you need extensions as there is none in this wordlist.
So you may try first to use this list for subdomains and/or domain names, it is a small list so the enumeration will be quick. However it won’t work.
So the only thing left that could make it word is to add extensions:
===============================================================
catsec@kali~$ gobuster dir -u 10.10.81.215 -w LogPose.txt -x html,php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.81.215
[+] Threads: 10
[+] Wordlist: LogPose.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2020/11/02 22:13:10 Starting gobuster
===============================================================
/dr3ssr0s4.html (Status: 200)
===============================================================
2020/11/02 22:14:11 Finished
===============================================================Yes, you get 1 result.
Conclusion — Page: /index.html
After a bit of decoding and a bit of OSINT, you successfully got the url of the next island.
Time to go there and see what it hides.
Page: /dressrosa.html
Info: /dressrosa.html is not the actual name of the page but let’s say it’s close enough.
By going to the recently discovered webpage, you arrive on this page:
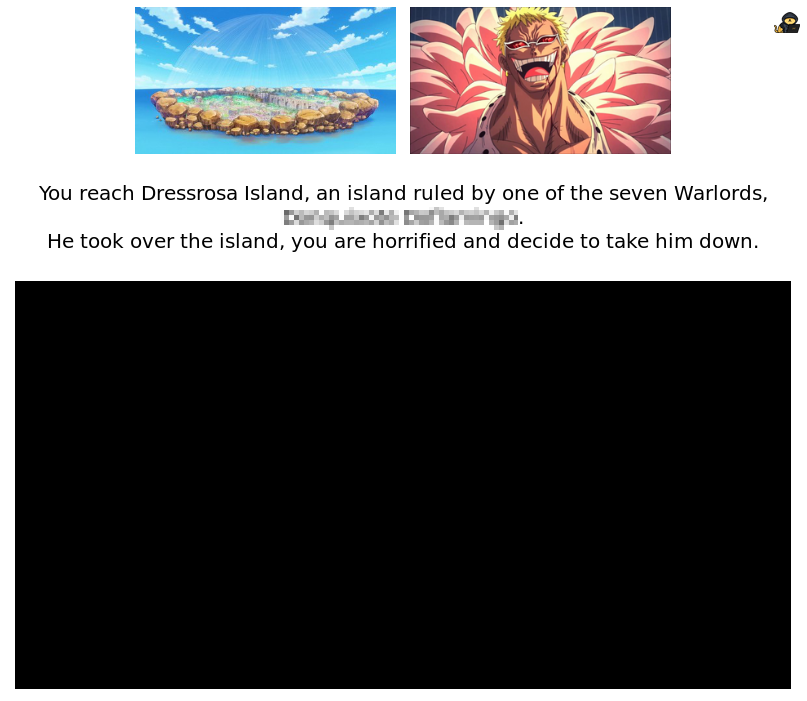
Info: Doflamingo being one of the most charismatic antagonists of the entire manga needed to be included in this box.
First interesting thing is that you get the answer to Task 2 Question 2 within the text itself.
Then, you can notice that whenever your mouse pointer passes above the black “image”, the black will disappear and let you see a part of the image that is behind it.
If you download the image behind, you will notice that it is named “rabbit_hole.png”.
If you look at it, here is what you will get:

Alright, so we have 3 encoded and/or encrypted strings.
Let’s find out what each of them means:
Decode/Decrypt
- First string:
This definitely looks like it is hex encoded so let’s decode it, we get:
key:im on oti oti - Second string:
This one looks like it is base91 encoded and if we decode it we get:
ito ito no mi:yek - Third string:
This one may be hard to identify at first sight but if we look at the 2 previous decoded strings, we see that they are the same, only reversed. You can also notice the word “key” so it suggests that you need a key to decrypt the third string.
Could the third string be vigenere encrypted ? What could be the key in this case ? “im on oti oti” or maybe “ ito ito no mi” ?
Well, if you know how a viginere encryption works, you should know that none of them can be the actual key as each of them contains spaces which are not allowed for a viginere key.
What if we try to decrypt the third string with both keys without spaces ?
With the key “imonotioti” we get: “Dvfgfhnnzo iz songq smankiil”
With the key “itoitonomi” we get: “Doflamingo is still standing”
Info: The “ito ito no mi” is the actual devil fruit eaten by Doflamingo in the Manga.
Good news, we cracked the third string.
Bad news, as the image name suggested it, this was a rabbit hole.
At this stage, you may be tempted to think about steganography on this image as this seems to be the only thing you can do but spoiler alert, you won’t find anything, this would just be another rabbit hole.
Source Code
Analyzing the source code is something that must be done in almost any pentesting situation. It can really give you valuable information. And I am pretty confident that it is something you do quite often too whenever you are performing a pentesting.
However, if you look at the source code of our webpage here, you won’t find anything really interesting (except for the rabbit_hole.png URL which proved to be very useful).
You need to dig deeper. And here you are lucky, there is no javascript involved or anything, there is only a CSS style sheet. By looking at it, you may come across something interesting:
#container {
height: 75vh;
width: 90vw;
margin: 1vh;
background-image: url("../king_kong_gun.jpg");
background-repeat: no-repeat;
background-position: center;
background-size: cover;
display: flex;
flex-direction: row;
justify-content: center;
align-items: flex-start;
align-content: flex-start;
flex-wrap: wrap;
position: relative;
}Another image is used as background on this webpage. But this image is generated through the CSS style sheet, that is why it’s not displayed on the html source code.
Info: This image is actually behind the “rabbit_hole.png” image which itself is behind the black boxes.
Remember, when we were on the webpage “/index.html”. An enumeration with a standard wordlist gives /images and /css. As you may have guessed, this CSS style sheet is located in the /css directory. Indeed this is the second way we talked about earlier, the one that could have been used to avoid the OSINT from the previous part. It is even a shortcut that would have lead you directly to the following part.
Steganography
Let’s download this image and give a look at it:

Info: In the Manga, this is the last punch Luffy throws at Doflamingo.
This seems like we need to do a bit of steganography once again.
Spoiler alert: This won’t be the last time you need to do some steganography in this box.
With a simple exiftool command, we can access the metadata and we get:
catsec@kali~$ exiftool king_kong_gun.jpg
ExifTool Version Number : 12.08
File Name : king_kong_gun.jpg
Directory : .
File Size : 42 kB
File Modification Date/Time : 2020:07:26 13:26:42+02:00
File Access Date/Time : 2020:11:02 22:19:36+01:00
File Inode Change Date/Time : 2020:11:02 22:19:26+01:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Comment : Doflamingo is
Image Width : 736
Image Height : 414
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 736x414
Megapixels : 0.305Interesting, a comment that gives us the location of another image.
By downloading and looking at this other image, we get:
Info: This is the actual image from the scan where Doflamingo gets hit by the attack of the last image. He got defeated.
Well, I did not lie with the previous image, it wasn’t the last time you would have to do some steganography within this box.
This time you need to use the strings command and the last line of the output will give you:
catsec@kali$ strings ko.jpg
.....
'8,6
<$cq,9r
Ts;}
Congratulations, this is the Log Pose that should lead you to the next island: /wh0l3_c4k3.phpSpoiler alert: Once again this won’t be the last time you need to do some steganography in this box but this will come later.
The interesting thing here is that you get the location of the next island, you can go there.
Conclusion — Page: /dressrosa.html
After a bit of code analysis and a bit of steganography, we got the location of the next island.
Page: /cake.php
Info: Same as before, /cake.php is not the actual name of the page.
By going to this webpage, you get:
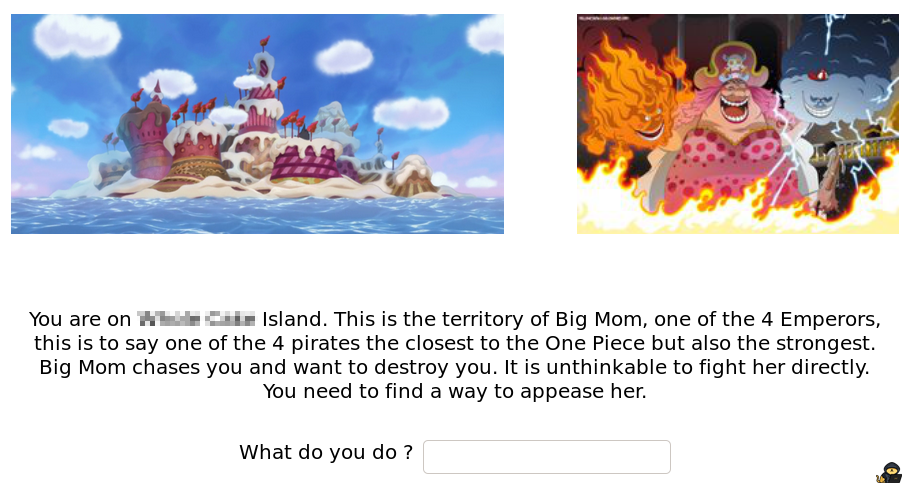
First thing first, the text itself contains the answer to Task 2 Question 3.
Then, you see you are on Big Mom’s territory. Big Mom ? Isn’t it the one that owns a Road Poneglyph according to the “.secret.txt” file we got from the FTP server ?
So there is a Road Poneglyph nearby, we need to find it.
Injection
The first thing that may come up to your mind seeing a page like this with an input form is: “Some sort of injection might work”.
So let’s try a bit:
Alright, I just tried to perform a basic RCE by submitting the command:
; ping <ATTACKER_IP>
However, I got a text displayed after submitting my command:
“I did not expect that.”
Could that mean the input is filtered ? That maybe, one of the character I used shouldn’t be used or maybe the command itself ? Is it vulnerable to another type of injection ?
If I wasn’t the room creator, in this case I would use burp and try to figure out how this form is used by the web server and I would try to find a way to exploit it somehow.
The goal would be to answer the following question:
Is it vulnerable to a specific type of injection ?
But I must confess, if I do this, I won’t find anything interesting.
Why ?
The reason is pretty simple, the php code checks whether you submitted something or not (empty string considered).
If you did, it will print out “I did not expect that.”.
However your input is not processed at all, it is a useless form that does nothing except printing its message whenever the form is submitted.
This is a rabbit hole.
How could you figure that out?
Test, test, test, test, test, test, test etc.
There are many things you can try but at some point you will realise that this can’t be exploited and you will move on.
Info: Also as it is precised in Task 1 description, there are rabbit holes. I hope it will hint people not to perform highly advanced level injection and not to lose too much time there.
Cookie Poisoning
By checking the source code of the webpage, you can see:
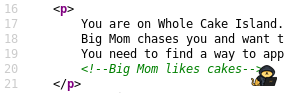
Info: In the Manga, Big Mom is crazy about cakes.
Could that be a hint for what needs to be done ?
Yes, it is.
Cakes is a hint for cookie.
The value is “NoCakeForYou”, not much to say that this is unusual.
Moreover, the source code comment was “Big Mom likes cakes”.
What if we edit the value and put “CakeForYou” instead ? Reload the webpage and you get the following text displayed below the form:
You successfully stole a copy of the 2nd Road Poneglyph: FUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJA
You succeed to run away but you don't own a Log Pose to go to Kaido's Island, you are sailing without even knowing where you are heading to.
You end up reaching a strange island: /r4nd0m.htmlNice, we got our second Road Poneglyph and we even got the location of the next island.
Info: The value of the edited cookie is irrelevant, you could have put whatever you want. As long as it is not “NoCakeForYou”, it will work just fine.
Conclusion — Page: /cake.php
After some cookie poisoning, you get the location of the next island and a copy of the second Road Poneglyph.
Info: As for the first Road Poneglyph, trying to decode it alone is pointless. You would just create yourself another rabbit hole.
Page: /arbitrary.html
Info: Once again, /arbitrary.html is not the actual name of the page.
By going to the webpage, you get:
Info: Buggy being the favorite character of Eichiro Oda, the manga artist who created One Piece, I had to include him in this room.
Alright, we get the answer to Task 2 Question 4 by reading the text.
Then you need to decide which game you want to play against him.
Let’s start with the brick breaker:
Brick Breaker
If you follow the brick breaker link, you will end up on this page:

And you will be able to play a brick breaker with your keyboard arrows if you want to chill out a bit.
If you lose, you will get this prompt:
Info: I’m truly sorry, I wrote this sentence in french and forgot to translate it into english, please forgive me…
It means: “Buggy won, would you like to play again ?”
By clicking “OK” you restart the game.
Alright, so there are 3 ways to solve this:
- The Adventurer
- The smart Slothful
- The smarter Slothful
- Let’s be an Adventurer first:
The first way to succeed this part is obviously to play the brick breaker and to finish it.
Info: I wish you all good luck if you want to follow this method. May the force be with you.
2. Then let’s be a smart Slothful:
If you modify the window width, you will notice that the paddle width is not modified, however, the bricks width is.
Hence you can modify your window width to adjust it to the size of the paddle and then launch the game which would guaranty you a victory without even playing, all you need is some time for it to finish.
Info: As you may have guessed, this behavior is due to the fact that brick width is calculated according to the window size while the paddle width is defined in pixels. You can also reduce your window height, it would finish the game faster.
3. Finally, let’s be a smarter Slothful:
Well, this game is coded with some javascript, what about just looking at the code and see what it does if we win ?
If you look at the js file, you will see:
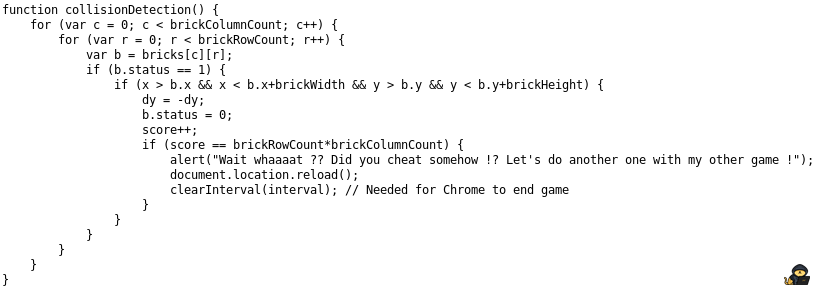
I won’t go into too much details about how this code works but with some basic javascript knowledge, you can see some interesting stuff:
So if your score equals the number of bricks per row multiplied by the number of bricks per column (meaning the total number of bricks), you get an alert.
Info: An alert is a prompt message, you may have already seen it if you already coded some stuff in javascript, or if you performed XSS exploits etc.
This message would be:
“Wait whaaaat ?? Did you cheat somehow !? Let’s do another one with my other game !”
Ok let’s prove we would get this prompt message if we successfully finish the game (I obviously used the smart Slothful method to do that):
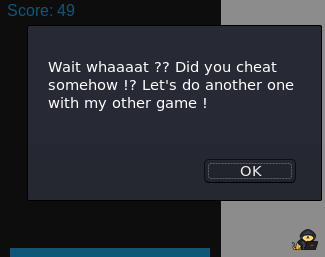
Yay, we finished the brick breaker !
The problem is, it was a rabbit hole.
Buggy seems to think we cheated somehow and wants to defy us on his other game. To be honest, if you modified the window size or if you looked at the code, Buggy is right, you cheated.
Brain Teaser
By following the Brain Teaser link, you get:
Info: As it is a brain teaser, there is no hint about what needs to be done.
But the first thing you notice is that the front face of the cube follows your mouse pointer. And whatever the position of your mouse, you can only see 5 faces of this cube. The face on the back will remain hidden.
The purpose of this brain teaser is to see what is on the back face of this cube.
Once again, for this game, you have 3 ways to see the back face of the cube:
- Window Size
- Source Code
- Document Object Model (DOM)
- Let’s start by playing with the window size:
If you load the webpage within a small window and if you then increase the size of the window, you will be able to make the cube rotate entirely with your mouse pointer.
Note that if you increase the width of the window, your back face will be upside down.
However, if you increase the height of the window, you can see the back face of the cube properly:

2. Now, let’s give a look at the source code:
If you look at the souce code of the html page directly, you won’t find anything interesting:
As you may have guessed, a webpage like this cannot be done only using CSS and HTML languages, a javascript script is used.
If you look at the javascript code, you will see:
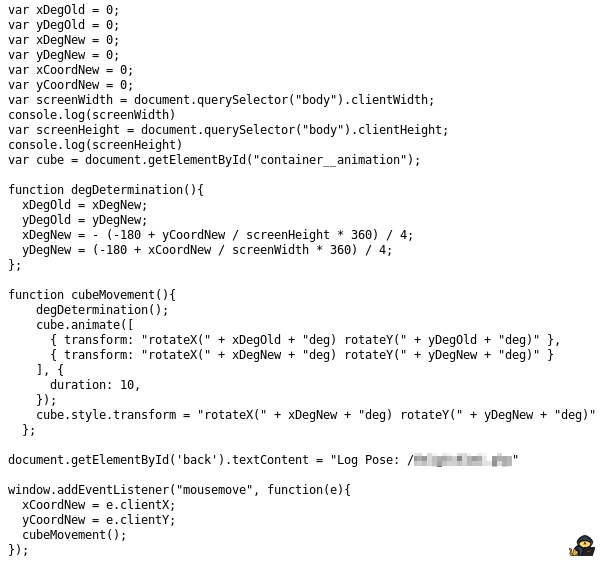
And you can see what is hidden on the back face of the cube.
Info: It could have been a good idea to check the CSS source code too as I could have decided to load the content of the back face thanks to the CSS (we remember that the interesting image from /dressrosa.html was loading thanks to its CSS style sheet).
3. Now let’s use the Document Object Model (DOM) to see the back face:
If you never programmed any website, you may not be familiar with what the DOM is. I can only advise you to learn about it, there are a lot of online ressources that can answer your question, for instance, the following webpage is a nice ressource:
https://developer.mozilla.org/en-US/docs/Web/API/Document_Object_Model/Introduction
Roughly, the DOM is a representation of your webpage for you to manipulate it. Actually, the javascript language allows you to interact with the DOM itself and that is why you can manipulate a webpage thanks to this language.
There are many ways to use the DOM to look at the back face of the cube, I’ll show you one but it is definitely not the only one.
For instance, you could change the position of the back face of the cube and put it at the place of the front face, or you could make everything transparent except for the back face etc. Possibilities are endless.
In our case, I will just show you how to get the value of the text incorporated within the back face of the cube, I won’t even manipulate the DOM. I will just retrieve a value thanks to him.
Alright, so let’s take a look first at the source code of our html webpage as we need to “select” the back face of the cube:
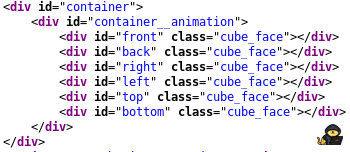
So we notice that the “id” of the back face is “back”. This is required to know in order to select this element in the browser console.
Now we need to open our browser console:
right click -> inspect element ->console (Firefox)
You will have something that looks like this:
To select the back face element, you need to type the following:
document.getElementById(‘back’)
As you know, “back” is the “id” of the back face.
Then you need to click on the small triangle on the left of the “div#back.cube_face” to display the element.
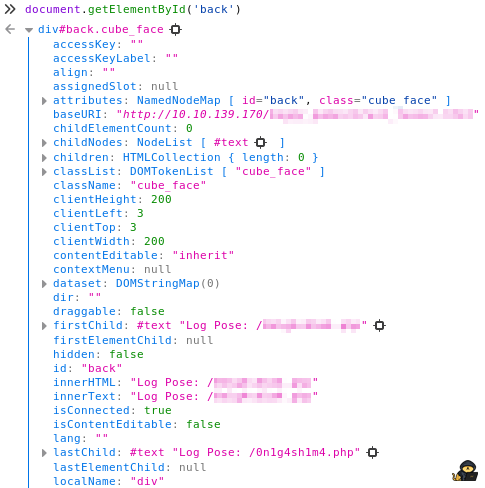
I won’t go into details but this is the DOM representation of the element having the “id” “back”. So in our case, it is the respresentation of the back face of the cube and you can find the text written on it here: “innerText”.
Info: This last method is probably the longest one and I guess no one will retrieve the back face text using this method. However, I thought it would be a good idea to introduce the DOM to any beginner who would read this as the DOM is one of the major concepts of web development.
Whatever the method you used to solve the brain teaser game, you should have found the Log Pose to reach the next island.
Indeed, as Buggy said, he gave you the Log Pose for Onigashima as you won.
Conclusion — Page: /arbitrary.html
Well, after playing a brick breaker for fun and solving a brain teaser, you successfully got the location of the next island.
Page: /onigashima.php
Info: Did you guess that this wasn’t the actual name of the webpage ?
By going to this webpage, you get:
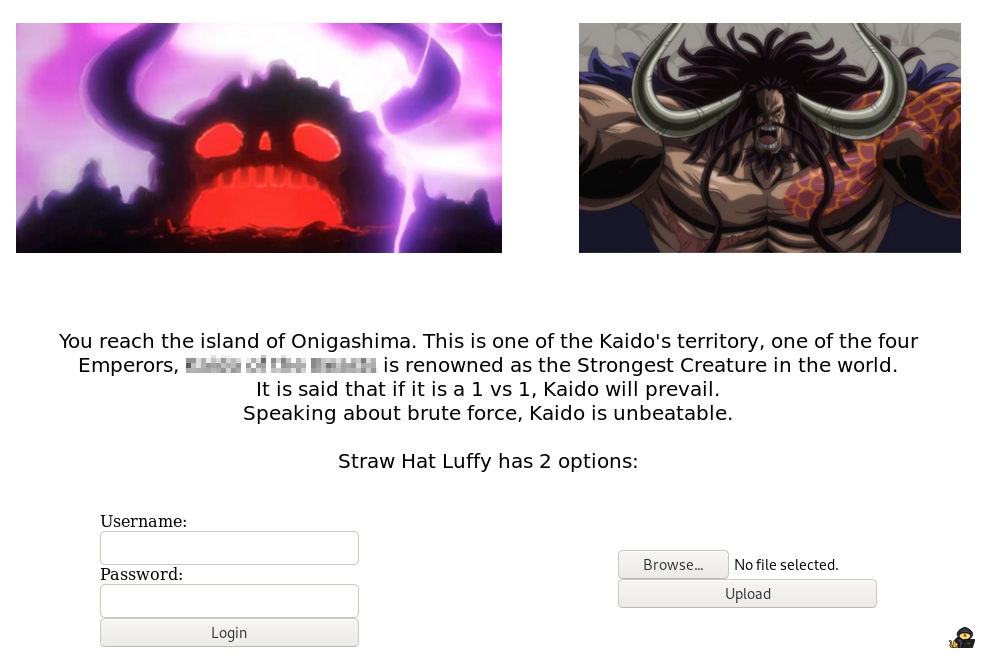
Kaido is the main antagonist of the current arc in One Piece. Not much to say that the One Piece community is currently living one of the most exciting moments of the entire manga.
Wait, according to the file “.secret_room.txt”, Kaido owns a Road Poneglyph. We must find it.
If you are on a webpage like this, you have several options but one of your first bets should be:
File Upload
Why would you try the file upload first rather than the login forms ?
Well, it is for the same reason as you did not try to brute force the SSH port at first. You don’t know the username and you don’t know the password either so brute forcing both would just take forever.
Whenever you want to upload a file, the 2 first questions that you must answer are:
1. What type of files (extension) can I upload ?
2. Where is stored the file on the server ?
The first question can usually be answered easily, all you need to do is to try to upload various files with different extensions and try to answer the following questions:
Does a php file work ?
If not, does another extension (php3, phtml etc.) which can execute php work ?
If not, does something like “file.jpg.php” work or maybe “file.php.jpg” ? etc.
The second question is usually even more easier as usually when you upload a file, you can access its URL directly after the upload either with a link or by looking at the source code.
Sometimes, if the website is using a CMS, you may perform some OSINT to find out where the files are stored by default.
Sometimes, you may need to dig deeper by enumerating the website or by analizing the behavior of the website using a tool like burp for instance.
In our case, you can upload whatever extension you’d like. I uploaded a file named “php-reverse-shell.php” in the following example:
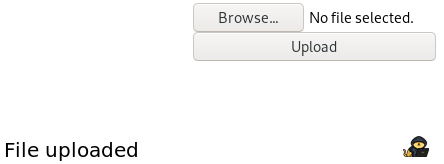
And as you can see when you upload it, you will have the text “File uploaded” that will be displayed. Perfect you answered the first question, there is no filter at all for a php extension.
However, it gets harder for the second question.
Where can you access it ?
Here, you don’t have a direct link to your file and the website is not using a CMS so the only choice left is to find out manually.
You could spend a bit of time trying to find out where it goes but let me help you a bit:
Your file cannot be accessed. It doesn’t even exist on the web server. This webpage lied to you, your file has not been uploaded.
Yes, sometimes, pirates lie.
This is just another rabbit hole.
Info: Once again, this form is useless and does nothing except printing out its message whenever you have selected a file and clicked on “Upload”.
Brute Force
Right now you may think you can’t do anything as the file upload is pointless and brute forcing both the username and password is definitely not appealing.
However, the text of the webpage itself says:
“Speaking about brute force, Kaido is unbeatable”
Could that be a hint ?
Let me ask you a question:
What can you try to brute force in a reasonable amount of time here ?
Seemingly nothing, is it the right answer though ?
Let’s give a look at the source code:
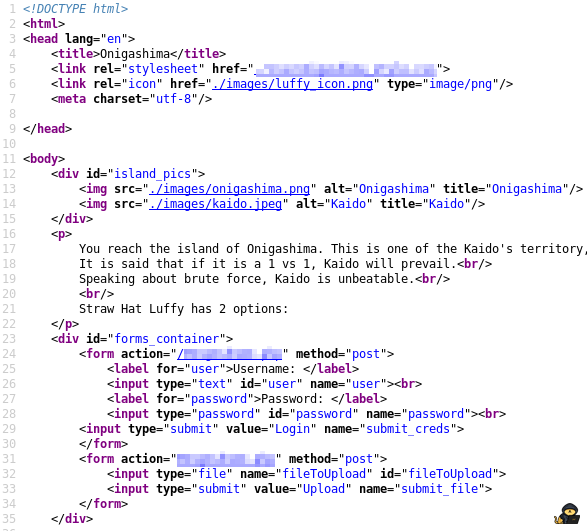
Anything that catches your eye ?
That may not seem obvious for beginners but kaido image is a jpeg format. Meaning you can try brute force it with a tool like stegcracker.
Info: I could have chosen to also include it in a png format as there are tools to brute force png format too. But I prefered to put it in jpeg because if you give a look at all the other pictures from the other web pages, they are all in png format making this one stands out.
It stands out even more if you gave a look at the /images directory and you may have cracked it from the beginning.
Spoiler alert: This is the last time we need to perform some steganography within this room, I promise.
So let’s download the image and let’s crack it (it may take up to 15 minutes), you get:
catsec@kali$ stegcracker kaido.jpeg ../Wordlists/rockyou.txt
StegCracker 2.0.9 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2020 - Luke Paris (Paradoxis)
Counting lines in wordlist..
Attacking file 'kaido.jpeg' with wordlist '../Wordlists/rockyou.txt'..
Successfully cracked file with password: imabeast
Tried 106436 passwords
Your file has been written to: kaido.jpeg.out
imabeastNice, it contains a username. We can now perform another brute force attack but on the login form this time.
So “ERROR” is displayed whenever the password is not correct.
Now, by looking at the source code or by firing up burp, we get the parameters we needed. We are now able to launch our brute force attack.
I used hydra but you can use any other similar tool if you’d like
And as you may have guessed, it was a success. The ouput is:
catsec@kali$ hydra -l K1ng_0f_th3_B3@sts -P ../Wordlists/rockyou.txt 10.10.81.215 http-post-form "/0n1g4sh1m4.php:user=^USER^&password=^PASS^&submit_creds=Login:ERROR" -t 64 -V
[ATTEMPT] target 10.10.81.215 - login "K1ng_0f_th3_B3@sts" - pass "kate123" - 17438 of 14344399 [child 52] (0/0)
[ATTEMPT] target 10.10.81.215 - login "K1ng_0f_th3_B3@sts" - pass "justin14" - 17439 of 14344399 [child 27] (0/0)
[80][http-post-form] host: 10.10.81.215 login: K1ng_0f_th3_B3@sts password: thebeast
[80][http-post-form] host: 10.10.81.215 login: K1ng_0f_th3_B3@sts password: poiuy
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-11-02 23:19:51If now we use these crendentials to login, we get the following output:
You successfully stole a copy of the 3rd Road Poneglyph: FYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LIKFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LIK
You succeed to run away and there is only one Road Poneglyph left to find to be able to reach Laugh Tale. Unfortunately, the location of this last Poneglyph is unspecified.
Perfect, we got the third Road Poneglyph. Only one left to be able to reach Laugh Tale !
Conclusion: Page /onigashima.php
After an unsucessful file upload and 2 brute force attacks, we finally got our hand on the third Road Poneglyph.
However, we don’t know yet where is the last one.
Bonus:
Info: Each web page name is a reference to the actual island where we meet the associated antagonist in the Manga, except for Buggy.
Fourth Road Poneglyph
You may wonder where is the last Road Poneglyph as nothing seemed to indicate its location.
Actually, something indicates where it is. It is a word game. Just give a look at the last sentence you got after logging in successfully.
The last sentence you get after brute forcing Kaido’s credentials is:
“Unfortunately, the location of this last Poneglyph is …”
The “…” is the actual location and if we go there, we get:
The last Road Poneglyphe: FUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LIKFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBOFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC4LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LJAFUWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFYWS2LJNEAXC2LJNFUFC2LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2IBNFUWS2LIKFUWS2LJNEAWS2LJNFUQC4LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWQULJNFUWS2IBOFUWS2LJAFYWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFYWS2LJNBIWS2LJNFUQC2LJNFUWSALRNFUWS2IBNFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALJNFUWS2CRNFUWS2LJAFUWS2LJNEAXC2LJNFUQC4LJNFUWSALJNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUFC2LJNFUWSALRNFUWS2IBOFUWS2LJAFUWS2LJNEAWS2LJNFUQC2LJNFUWSALRNFUWS2IBOFUWS2LI=
Info: My first thought was to create a subdomain named “…” where the index.html file would have been the last Road Poneglyph but I thought it would have been too hard for the room I intended to create. That’s why the word game gives you the web page directly instead of the subdomain.
Road Poneglyphs Message
According to the file “.secret_room.txt” we got from the FTP server:
- Each of the Road Poneglyph gives one of the keys to reach Laugh Tale.
Each Road Poneglyph alone is useless but all of them together reveals the meaning.
So you need to concatenate them all. The string you get seems to be base32 encoded, let’s decode it, we get:
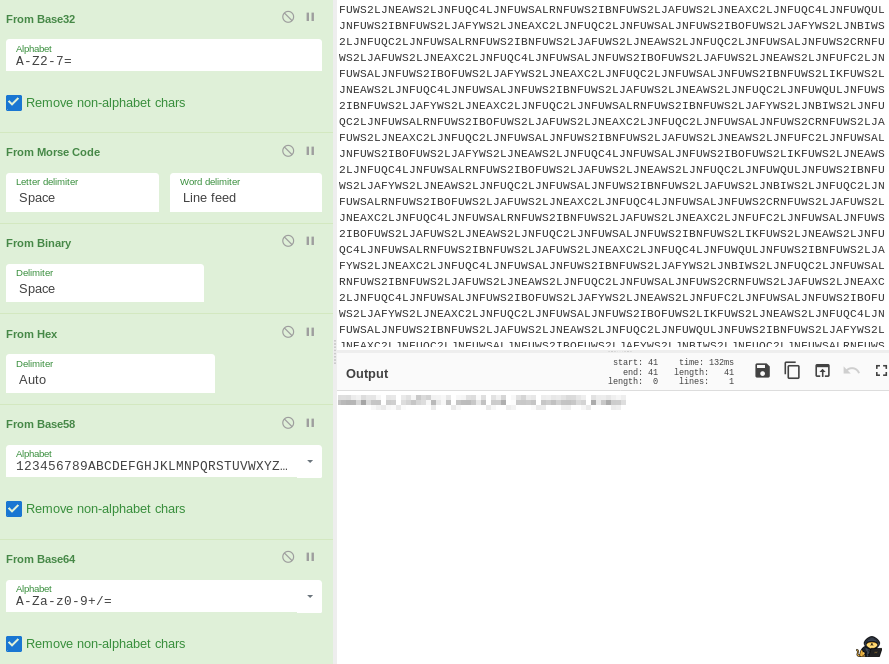
M0nk3y_D_7uffy:1_w1ll_b3_th3_p1r@t3_k1ng!
Well it is obviously obfuscated on this screenshot as you get the credentials of a user in the format <USER>:<PASSWORD>
This is also the answer to Task 2 Question 6.
You are now able to use them to reach Laugh Tale, the final island where the One Piece is located.
Conclusion: Road Poneglyphs Message
Finally, it was a long way to be able to reach Laugh Tale. But who said that becoming the Pirate King was an easy task.
However, are you the Pirate King yet ?
Let’s use the credentials to log through the SSH service to find out.
Laugh Tale
Alright, so when you log in. You’ll reach luffy’s home directory.
Info: The actual username is not luffy, however it is the name of the group user.
If you list the home directory, you get:
catsec@kali$ ssh M0nk3y_D_7uffy@10.10.81.215
The authenticity of host '10.10.81.215 (10.10.81.215)' can't be established.
ECDSA key fingerprint is SHA256:zOHT7dbvRJlqSe19yomTmKvQHVgvwDLd7X8gGWScz84.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.81.215' (ECDSA) to the list of known hosts.
M0nk3y_D_7uffy@10.10.81.215's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-041500-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
18 packages can be updated.
13 updates are security updates.
Last login: Fri Aug 14 15:23:58 2020 from 192.168.1.7
M0nk3y_D_7uffy@Laugh-Tale:~$ ls -la
total 56
drwxr-xr-x 8 M0nk3y_D_7uffy luffy 4096 Jul 29 07:32 .
drwxr-xr-x 4 root root 4096 Jul 26 07:54 ..
-rw------- 1 M0nk3y_D_7uffy luffy 14 Aug 14 15:25 .bash_history
-rw-r--r-- 1 M0nk3y_D_7uffy luffy 220 Jul 26 07:54 .bash_logout
-rw-r--r-- 1 M0nk3y_D_7uffy luffy 3771 Jul 26 07:54 .bashrc
drwx------ 11 M0nk3y_D_7uffy luffy 4096 Jul 29 07:21 .cache
drwx------ 11 M0nk3y_D_7uffy luffy 4096 Jul 29 07:15 .config
drwx------ 3 M0nk3y_D_7uffy luffy 4096 Jul 29 07:21 .gnupg
-rw------- 1 M0nk3y_D_7uffy luffy 334 Jul 29 07:14 .ICEauthority
-rw-r--r-- 1 root root 283 Jul 26 08:23 laugh_tale.txt
drwx------ 3 M0nk3y_D_7uffy luffy 4096 Jul 29 07:14 .local
drwx------ 5 M0nk3y_D_7uffy luffy 4096 Jul 29 07:15 .mozilla
-rw-r--r-- 1 M0nk3y_D_7uffy luffy 807 Jul 26 07:54 .profile
drwx------ 2 M0nk3y_D_7uffy luffy 4096 Jul 29 07:21 .ssh
M0nk3y_D_7uffy@Laugh-Tale:~$ cat laugh_tale.txt
Finally, we reached Laugh Tale.
All is left to do is to find the One Piece.
Wait, there is another boat in here.
Be careful, it is the boat of Marshall D Teach, one of the 4 Emperors. He is the one that led your brother Ace to his death.
You want your revenge. Let's take him down !By reading this, you will find the answer to the Task 3 Question 1.
Info: In the Manga, the pirate Teach is the one who defeated Luffy’s brother and who delivered him to the Navy. Following this event, Luffy’s brother has been sentenced to death. Teach is considered by a lot as the final antagonist of the Manga. Others believe that the final arc will be to take down the World Government.
Now that you are logged in, you obviously want to escalate privileges.
You can use an enumeration tool such as linpeas if you wish to but I won’t as the vectors to escalate your privileges are pretty obvious and easy to find.
The first thing I like to do is to check the standard users of the machine. You can do it by checking the passwd file with a command like:
cat /etc/passwd
You get:
M0nk3y_D_7uffy@Laugh-Tale:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin
avahi-autoipd:x:106:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
cups-pk-helper:x:110:116:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
whoopsie:x:112:117::/nonexistent:/bin/false
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:114:119::/var/lib/saned:/usr/sbin/nologin
pulse:x:115:120:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
avahi:x:116:122:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
colord:x:117:123:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false
geoclue:x:119:124::/var/lib/geoclue:/usr/sbin/nologin
gnome-initial-setup:x:120:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:121:125:Gnome Display Manager:/var/lib/gdm3:/bin/false
7uffy_vs_T3@ch:x:1000:1000:Laugh-Tale,,,:/home/teach:/bin/bash
ftp:x:122:127:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
sshd:x:123:65534::/run/sshd:/usr/sbin/nologin
M0nk3y_D_7uffy:x:1001:1001:,,,:/home/luffy:/bin/bashSo we can see that the default shell of 2 lines is /bin/bash meaning that those are actual users. Right now you are the one obfuscated.
Generally in CTF challenges, if you have several users , you will need to escalate to one (horizontal escalation), then another one and so on until being root (vertical escalation).
Wait, so less can be run as root ? It’s gonna be easy.
Let’s give another look to gtfobins:
https://gtfobins.github.io/gtfobins/less/
You will see:
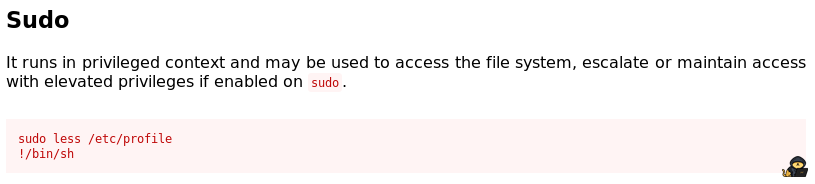
https://gtfobins.github.io/gtfobins/less/
Easy, let’s do it and we get:
7uffy_vs_T3@ch@Laugh-Tale:/$ sudo less /etc/profile
Sorry, I can't tell you where is the One Piece
7uffy_vs_T3@ch@Laugh-Tale:/$ Well, that is definitely not the behavior we were expecting.
This doesn’t look like the less command we are used to.
At this point, you have 2 main options:
- You transfer it to your own machine to analyze it deeper with better tools.
- You analyze it on the remote computer with the available tools.
You will always get more information about how a program works by analyzing it with your own tools such as ghidra, gdb etc., so let’s try to transfer it
Ah it doesn’t work, we could have foreseen it by looking at the file permission:
Indeed, the file doesn’t have read permission for other users so it cannot be extracted. But an executable without a read permission ? That’s unusual.
Moreover, we can notice that it has the write permission for other users. Hmm, this is even more unusual, we need to dig that deeper.
What about trying to write a bash script to get a reverse shell and then launch it with sudo ?
I take an simple bash script to get a reverse shell from the following website:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
In the script, I put my IP and the port 1234 which is the one I decided to use and now it is time to overwrite the “less” file.
Ahh it doesn’t work. But we have a write permission, how is it possible that we can’t write in this one ?
If you have never heard about what follows, this behavior may seem very strange.
Indeed, you have the write permission so in theory you can edit the file. But have you ever heard about file attributes ?
If not, I can only advise you to learn about it online, the following website is a nice ressource for instance:
https://wiki.archlinux.org/index.php/File_permissions_and_attributes
If you have write permission for a file but are not able to overwrite it, there can only be one explanation:
There is an attribute that prevents it.
Info: If you have the read permission for a file, you can use the command “lsattr” to list its attributes. In this case it won’t work as you don’t have this permission.
In this situation, 2 attributes are possible and can explain this behaviour:
- i for “immutable”
- a for “append only”
The good thing is that it is pretty easy to know which attribute is set on the file but we’ll come back to that right after because there is something important to notice first.
Here the file “less” is in the /usr/local/bin directory meaning it should be a binary. And you should know that playing with a binary is almost never a good idea.
But is it really a binary ? This could be a mistake from the system administrator.
I mean, being in a binary directory doesn’t mean that the file must a binary after all, it’s just a standard rule.
So let’s learn a bit more about the file with the following command:
So it is definitely not a binary, it’s just a simple “regular file” which is executable.
You can guess what language has been used to write this file thanks to 3 information you previously got:
1. It is not a binary
2. The sudo command is “sudo /usr/local/bin/less” and not something like “sudo /usr/bin/python3 /usr/local/bin/less” so probably a shell language (because it can’t be a binary)
3. Thanks to your previous “cat /etc/passwd” you know that the default shell used by root is /bin/bash.
It seems very likely that the “less” file is written in bash.
Now we can check which attribute is set on the “less” file.
Basically, if the attribute that is set is the immutable (“i”) one, you can’t do anything. Whatever you try, it won’t work because the file is immutable.
However, if the append only attribute (“a”) is the one that is set, you will be able to add “>>” at the end of a command that generates an output on the standard output. This output will be appended to the end of the file.
So let’s try to append something, if it works, it means that the “a” attribute is set, else it is the “i” one.
I can now use the same bash scipt as before to get a reverse shell but this time I will append the data with “>>”:
It worked ! So the append only attribute was set.
Let’s set the nc listener on the port 1234 as this is the port we used in the script and let’s try to run the script as sudo, we get:
Perfect we are now root !
In case you still have doubts regarding our previous hypothesis:
All is left to do now is to find the One Piece.
One Piece
Your first guess might be to go to the root directory to find the One Piece, but you won’t find anything there.
Same if you search a file named “OnePiece” (or something similar) through the entire file system, you wouldn’t find anything.
You can deduce that you need to check the content of each file.
You may be tempted to launch this type of command to be able to find it:
However, I should warn you. If you launch this, your grep command will look at each and every file on the file system trying to find the string “One Piece” (case insensitive). In other words, it will take aegis for it to finish.
It is smarter, to search only through specific directories with a command like this:
You then get a mysterious file that stands out, let’s call it “one_piece.txt” (obfuscated on this image).
By looking at the content of this file we get:
root@Laugh-Tale:/# cat /usr/share/mysterious/on3_p1ec3.txt
cat /usr/share/mysterious/on3_p1ec3.txt
One Piece: S3cr3ts_0f_tH3_W0rlD_&_0f_Th3_P@st$
root@Laugh-Tale:/#This file contains the answer to Task 3 Question 3.
Congratulations, you found the One Piece !
After finding the One Piece, you fulfilled your dream and became the Pirate King.
